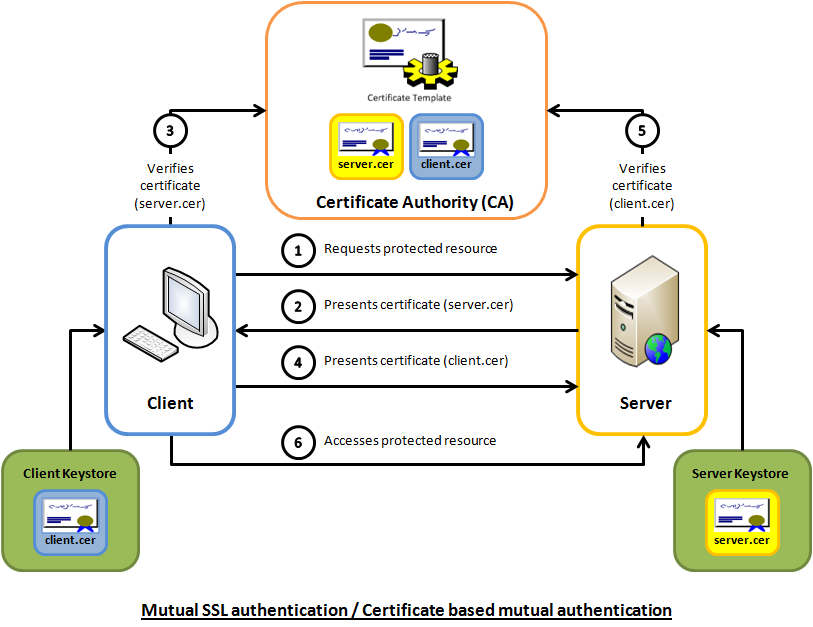
I am implementing mutual authentication between a single client hosted app (CLIENT) and my spring boot 2 application (SERVER). I understand the steps to be as follows:
The server generates a keystore and truststore. The keystore being used for storing the server's certificates and private key. The truststore used for storing other credentials (certificates from certificate authority (CA) or trusted client certificates).
A CSR is raised for the server which is then passed to a CA. The CA generates a signed certificate from the CSR. This is the installed in the server keystore.
- The client (which has it's own keystore and truststore) provides their public key to the server. This is then installed in the server truststore.
When a https request is made from client to server:
- The client makes a request to access a protected resource.
- Server responds with their public certificate.
- Client verifies that certificate (looks in truststore and checks if it signed by a trusted CA).
- Client presents their public certificate to server.
- Server then verifies certificate against their truststore.
- Assuming verification success client is granted access to the protected resource.
So I have a few things which I'm a bit confused about...
- Are the steps outlined above broadly correct?
- How does the server verify the client certificate? (I think it looks at the truststore for that certificate but not sure what actually happens after that).
- I've seen examples of the CA certificate being installed in the server truststore instead of the actual client's public certificate ~ is there a use case when this should or should not be done? For my use case I have been provided with a signed certificate from the client (third party). The CA who signed that is different from the CA who signed the server certificate.
- Does this process actually authenticate the client i.e. this client can now have access to the servers protected resources but another client who might present a different certificate will not have access? (like a more secure method of providing a username and password)
- Where does common name (CN) checking come into all of this? I note in Spring Boot X.509 you can derive a username from the CN and then use this to lookup the appropriate user details from the user details service.
- If the client certificate gets compromised for whatever reasons is this managed by just removing it from the server's truststore?
- Is there an advantage, in my scenario of using a trusted CA e.g. verisign to produce a client certificate over a self-signed one? i.e. the certificate is passed to me directly from the trusted third party, and then installed.