I am trying to establish a TLS mutual authentication with third party API. Client certificate is configured fine and when I try to access the end point url through Chrome it works fine(Chrome asks to confirm the certificate in a message box and when I does it the page displays with its content).
Same thing when I try to do with IE it is not working and showing this message
Cannot securely connect to this page
This might be because the site uses outdated or unsafe TLS security settings. If this keeps happening, try contacting the website’s owner.
Your TLS security settings aren’t set to the defaults, which could also be causing this error.
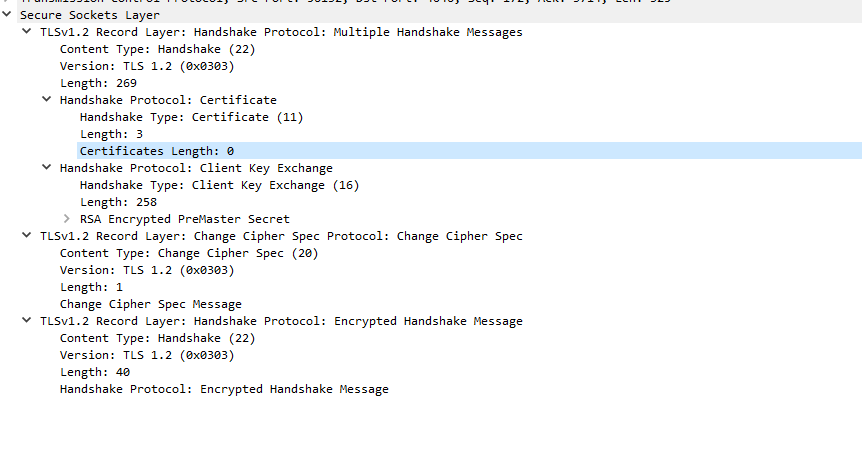
So I logged the details to Wireshark, And this is how it looks
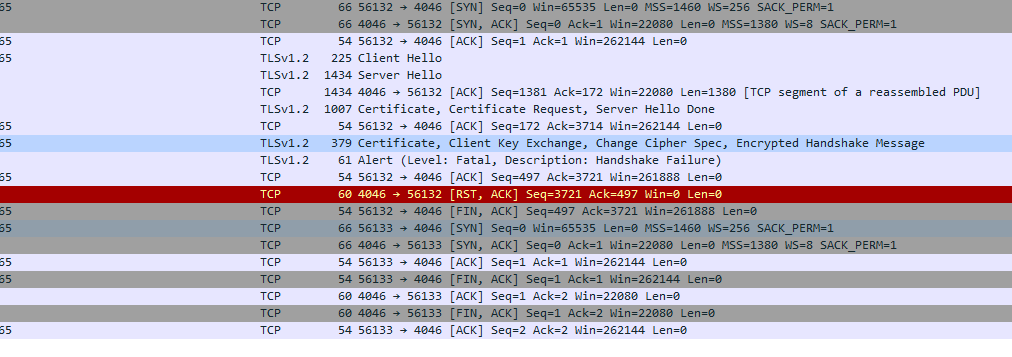 When I digged more in to details I can see that the client certificate was never sent on step 9(TLSv1.2 379 Certificate, Client Key Exchange, Change Cipher Spec, Encrypted Handshake Message).
When I digged more in to details I can see that the client certificate was never sent on step 9(TLSv1.2 379 Certificate, Client Key Exchange, Change Cipher Spec, Encrypted Handshake Message).
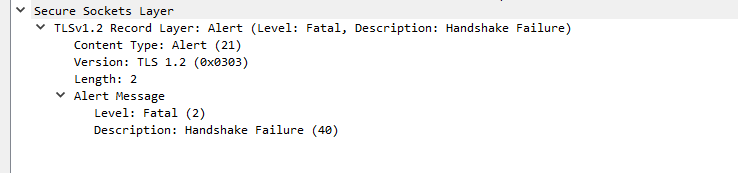
And in Step 10 this is the error I am getting
What can be the reason behind this behavior?
Update: When I try to access smae end point through code and checked SChannel logs, I can see a warning like this
The remote server has requested TLS client authentication, but no
suitable client certificate could be found. An anonymous connection
will be attempted. This TLS connection request may succeed or fail,
depending on the server's policy settings.