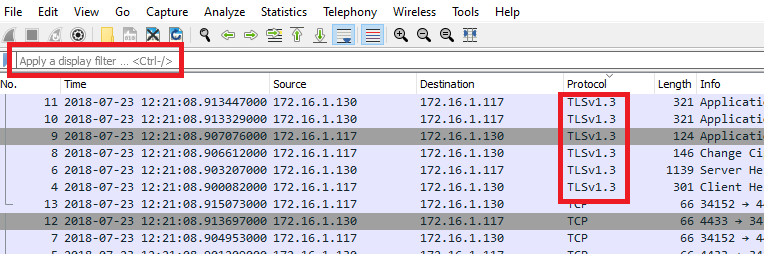
There is no easy filter for TLSv1.3 given that TLSv1.3 tries to masquerade as TLSv1.2 for compatibility reasons.
Current as of 2020-10-05 (Wireshark may add this at some point)
Wireshark
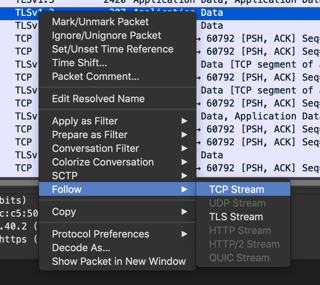
In Wireshark, you can follow this TLSv1.3 stream by right clicking on a packet in the stream and then adding && tls to see only TLSv1.3 packets in the stream (tcp packets will show up in the stream). Together, this should be something like tcp stream eq 0 && tls.
![Following stream]()
tshark
You can find this display filter easily with this bash script:
#!/bin/bash
filename=YOUR_PCAP.pcap
tcp_streams="$(tshark -r $filename -T fields -e tcp.stream \
-Y 'tls.handshake.extensions.supported_version == 0x0304' | sort | uniq)"
display_filter="tls && ("
first_stream="true"
for s in $tcp_streams; do
if [ $first_stream == "true" ]; then
first_stream="false"
else
display_filter+=" || "
fi
display_filter+="tcp.stream eq $s"
done
display_filter+=")"
printf "Display filter for TLSv1.3:\n$display_filter\n"
Here, we
- Get a sorted list of TLSv1.3 stream numbers
- Iterate over those streams so that the display filter will look like
tls && ($stream1 || $stream 2 || ...)
Creating your own Display Filter with Lua
Per the same question asked on Wireshark forums, there is a lua script that will do the same legwork as this bash script. This is a part of Wireshark documentation and is provided as example code which you could modify to your needs.