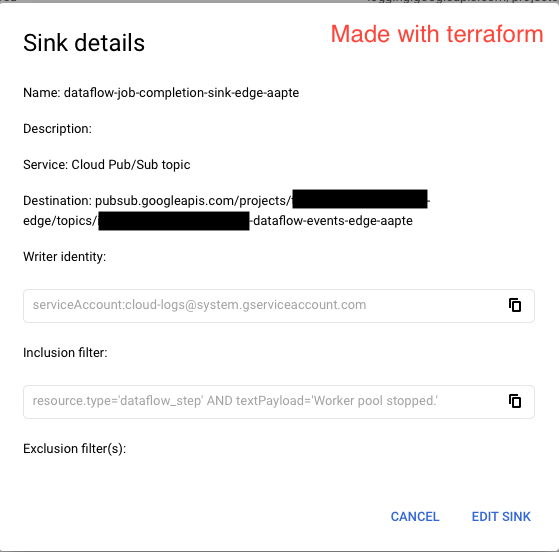
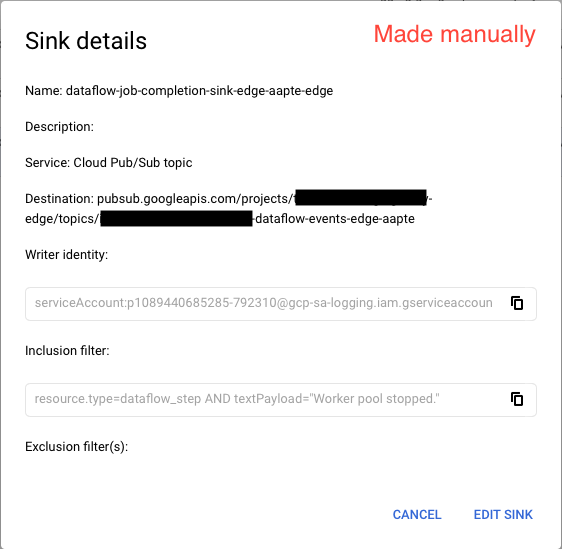
I want to create a Log Sink to listen to a specific message in Stack Driver and push the event to a Cloud Pub/Sub, which will trigger a Cloud Function.
Here is a part of my Terraform template.
resource "google_pubsub_topic" "dataflow_events" {
name = join("-", concat(["dataflow-events", var.environment, terraform.workspace]))
}
resource "google_logging_project_sink" "dataflow_job_completion_sink" {
name = join("-", concat(["dataflow-job-completion-sink", var.environment, terraform.workspace]))
destination = "pubsub.googleapis.com/projects/${var.project}/topics/${google_pubsub_topic.dataflow_events.name}"
filter = "resource.type=dataflow_step AND textPayload=\"Worker pool stopped.\""
}
Terraform version = 0.13.3
This gets deployed without any errors. However, no events are pushed to the Pub/Sub topic.
However, when I create the sink manually (from the Cloud Web Console), it pushes messages to the (same) Pub/Sub topic.
Here are two screenshots of two sinks.
Note: Changing unique_writer_identity parameter (either true or false) on both of them doesn't change its behavior. We used unique_writer_identity as true when we created the manual sink and that's why it has a global service account. But setting this to true in Terraform doesn't push messages to Pub/Sub.
Your expertise is highly appreciated.