I am unsure why public VIF must be used in AWS Direct Connect + VPN setup. Usually if you are connecting to Virtual Private Gateway you should use private VIF as shown in AWS Managed VPN. Why public VIF must be used in this case?
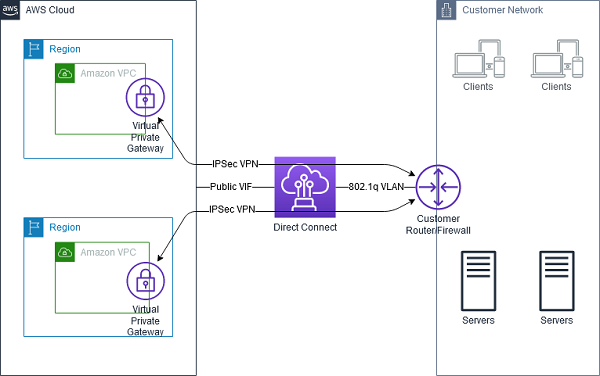
Diagram on AWS Direct Connect + VPN:
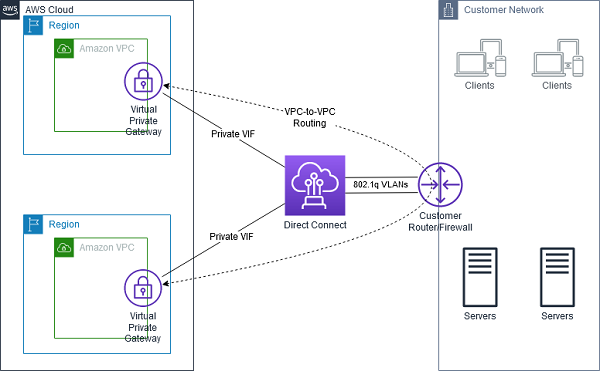
Diagram on AWS Managed VPN:
Edit 1:
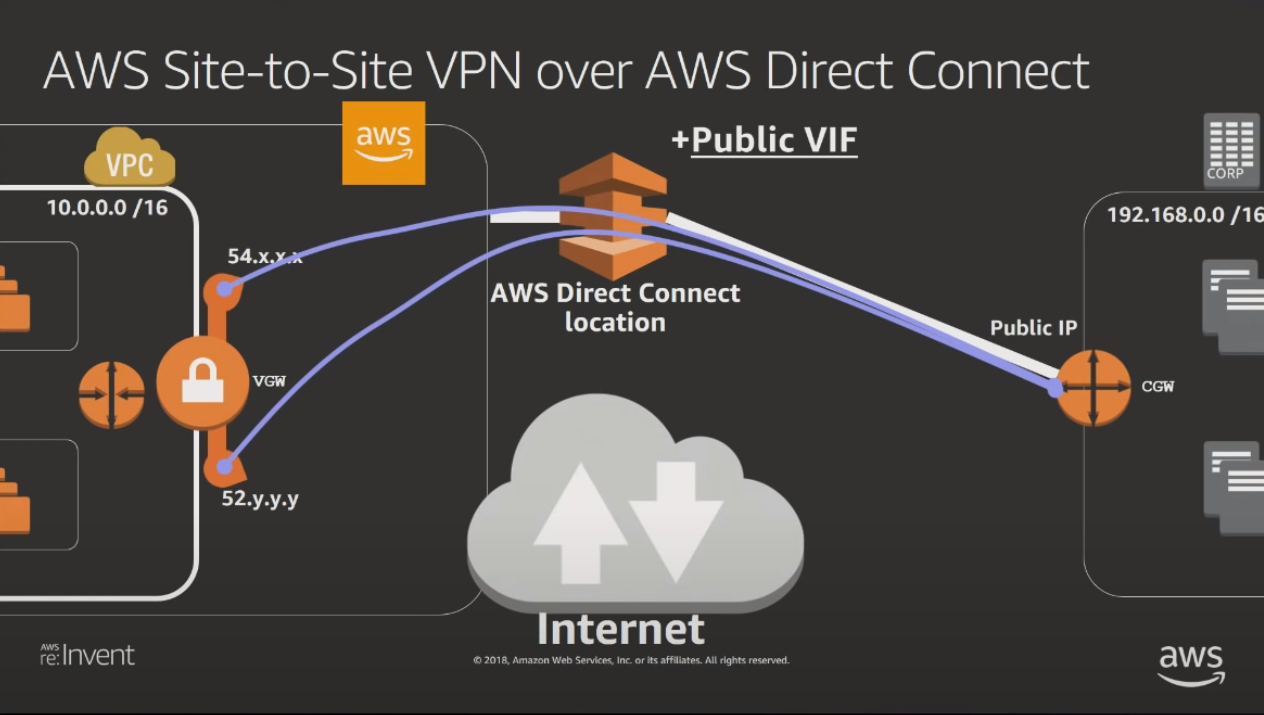
Got a better understanding by watching AWS re:Invent 2018: AWS VPN Solutions (NET304). We need public VIF because AWS Site-to-Site VPN creates two public endpoints on a Virtual Private Gateway which are visible to public VIF only. Diagram from that talk: