The error means the service principal used in your Azure DevOps service connection does not have enough permission to perform the action.
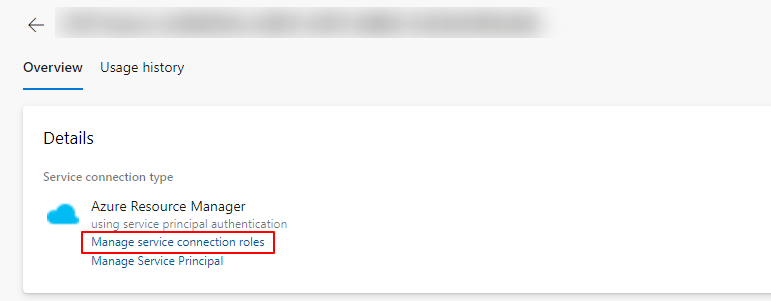
To solve the issue, you need to add an Azure RBAC role for the service principal, navigate to the Project Settings in Azure DevOps -> Service connections -> find the service connection you used(whose type is Azure Resource Manager) and select it -> select Manage service connection roles.
![enter image description here]()
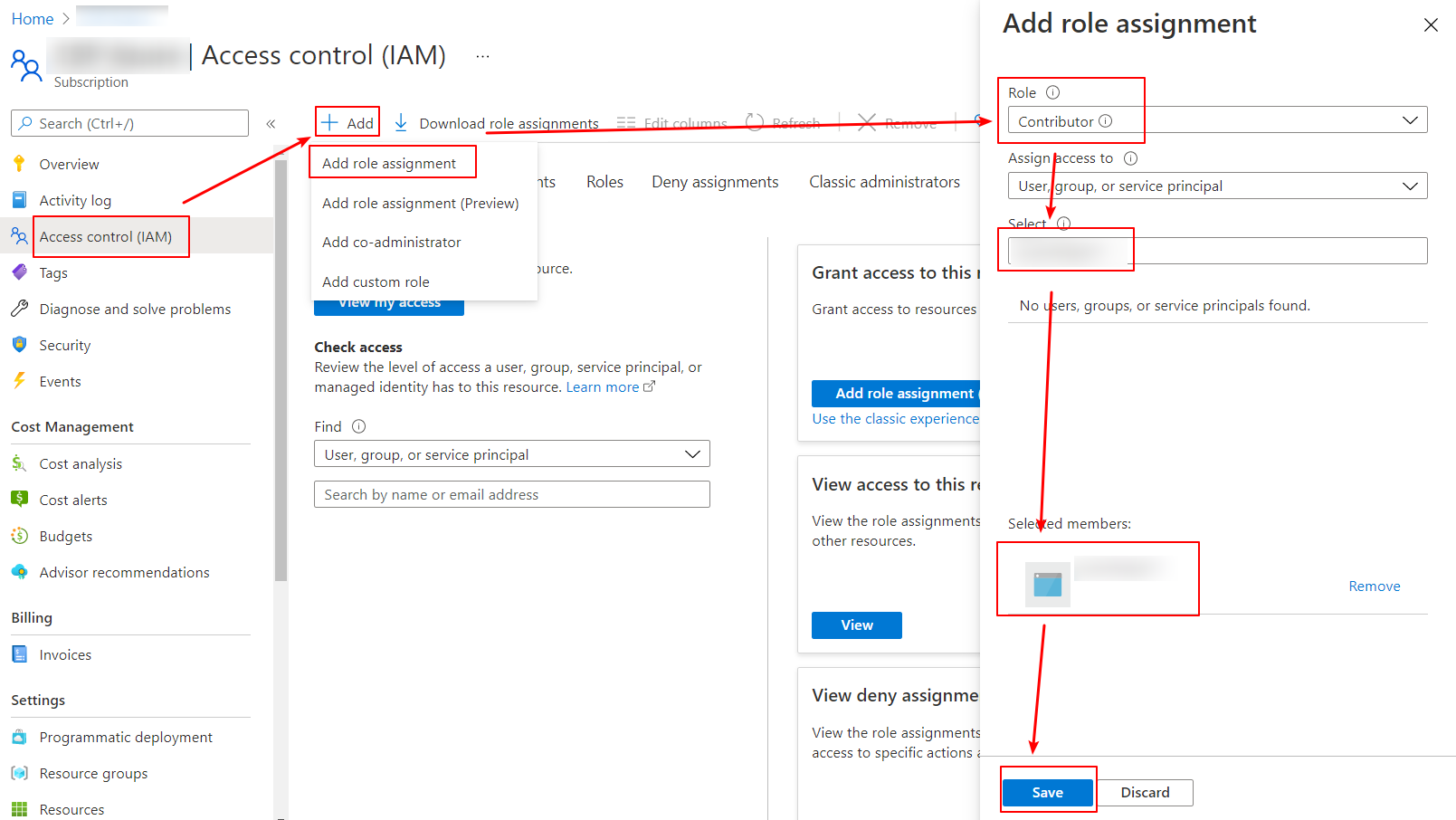
Then it will open a page for the Azure subscription in Azure portal, navigate to the Access control (IAM) -> add your service principal as a Contributor role as below.
Note: To assign the role for your service principal, your user account logged in Azure portal needs the RBAC role e.g. Owner, User Access Administrator.
![enter image description here]()