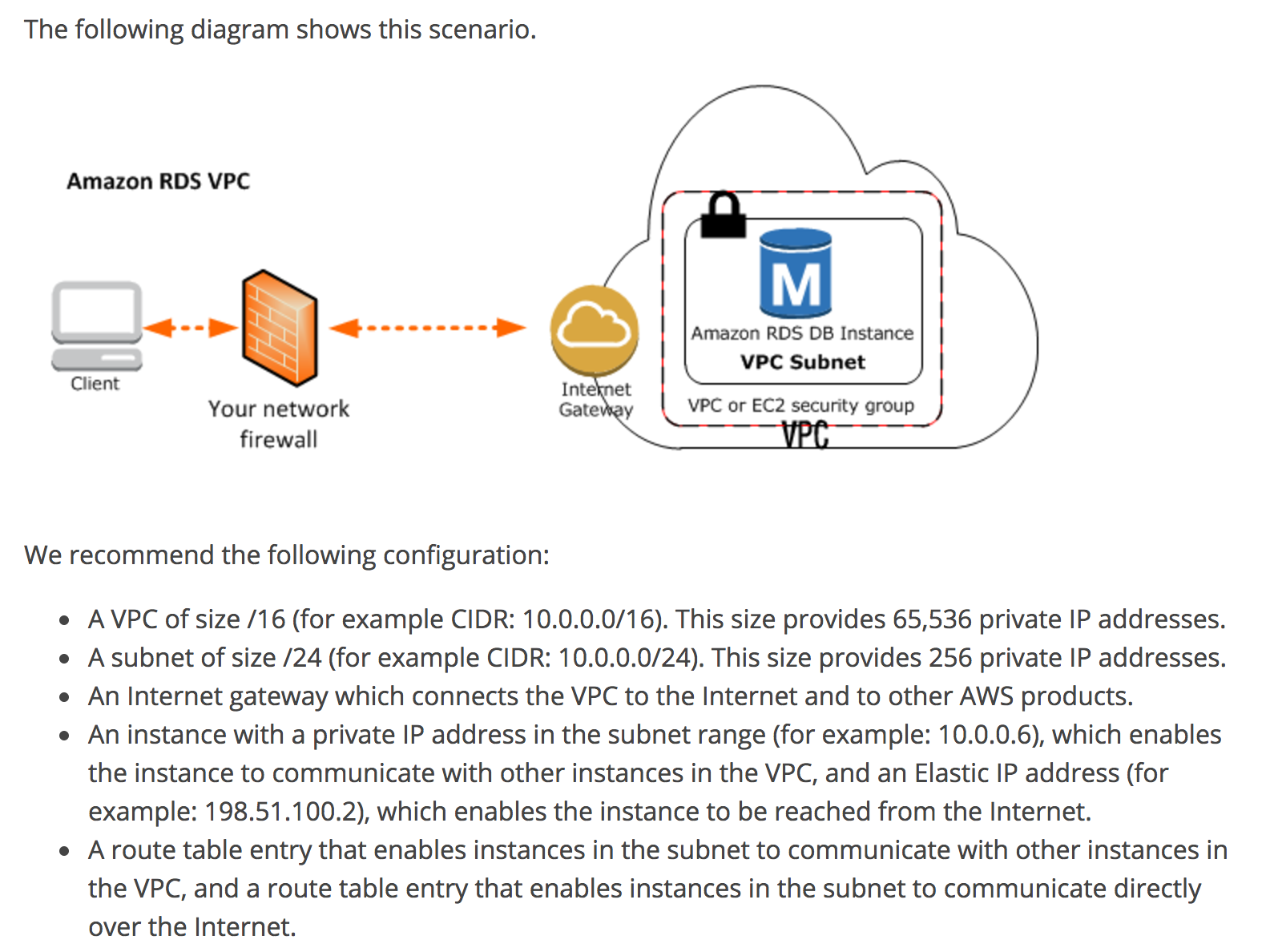
I have a VPC configured with 3 X public and private subnets and an IGW for the public, NAT Gateway for the private.
When I create an RDS instance, I flag it as publically available. When I try to access the RDS endpoint, my connection fails.
I have created a security group to allow all traffic: 0.0.0.0/0, my VPC allows traffic coming from my network.
If I place my RDS in the public subnet, then I can connect as the IGW allows the connection. But when it is placed in the private subnet, the connection fails?
I have reviewed a fair bit of material on AWS and forums - but I cannot seem to finalise the connection. Is there something I am missing in the configuration?
Any help would be greatly appreciated.
Cheers.