I can not produce a "Bus error" with the following assembly code. Here the memory address I use is not a legal "canonical-address". So, how can I trigger that error?
I was running this snippet of code under Ubuntu 20.04 LTS with NASM 2.14.02, but it results in a SIGSEGV segmentation fault on the load, not SIGBUS.
global _start
section .text
_start:
mov rax, [qword 0x11223344557788]
mov rax, 60
xor rdi, rdi
syscall
Corresponding X86-64 assembly code after compiling:
Disassembly of section .text:
0000000000401000 <_start>:
401000: 48 a1 88 77 55 44 33 movabs 0x11223344557788,%rax
401007: 22 11 00
40100a: b8 3c 00 00 00 mov $0x3c,%eax
40100f: 48 31 ff xor %rdi,%rdi
401012: 0f 05 syscall

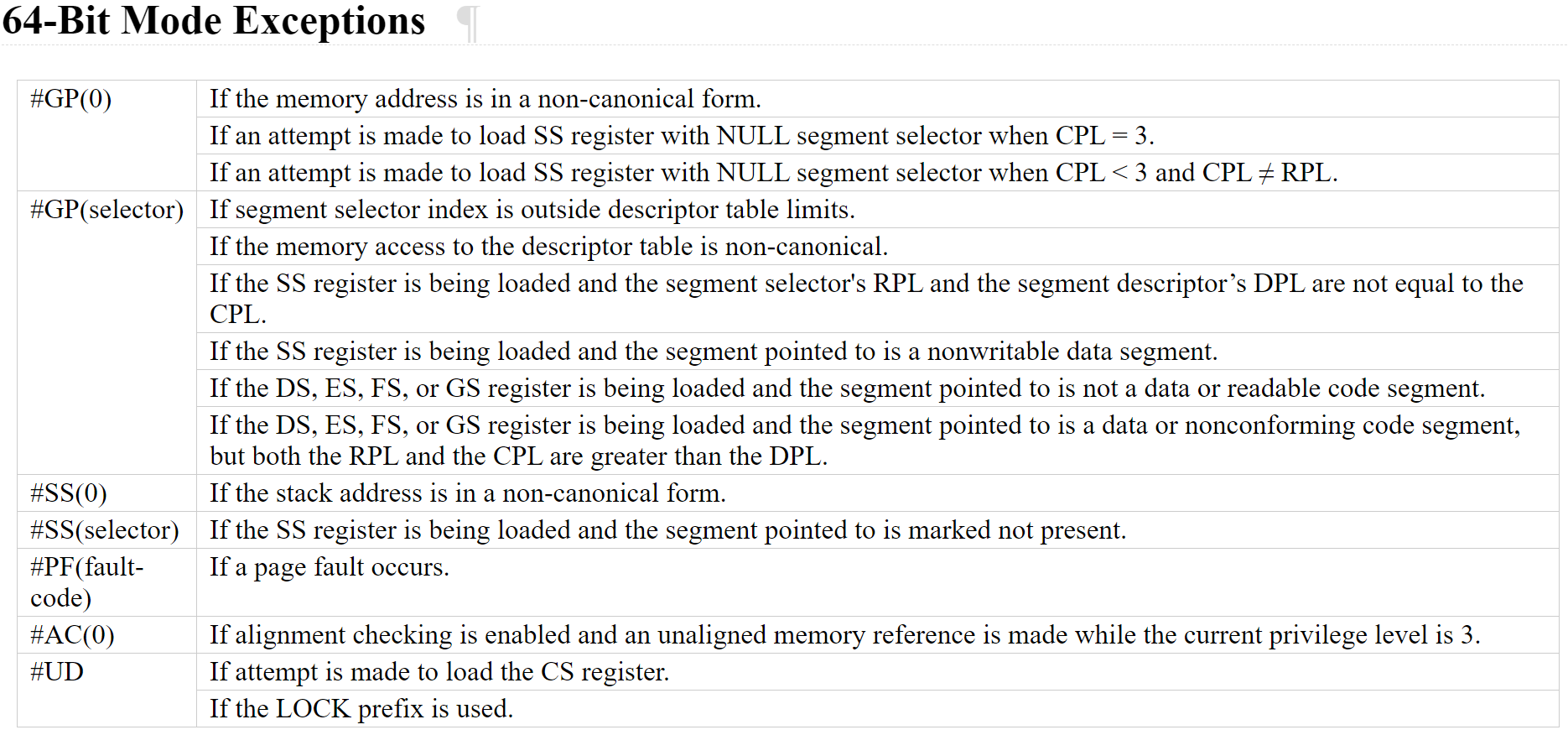
killsystem call to deliver aSIGBUSto yourself? – Dromedarymmaped page if the underlying file has been truncated, and you can of course use asm to make the system call to make that happen. Or of courseraise(SIGBUS). I think there is some kind of x86 exception (other than that special case of #PF) that the OS handles by delivering SIGBUS; possibly alignment-checking#AC, if you had a kernel module enable the AC flag? – Stifflerkill(getpid(), SIGBUS)ortgkillis a trivial answer. – Stiffler-EINVALfrom mmap if you tried withMAP_FIXED. – Stiffler#PFinstead of#GPeven if the kernel hadn't enabled that bit? – Stiffler