I wrote a program that generated an html file with this header:
but I don't have iframe at all, let alone in sandbox
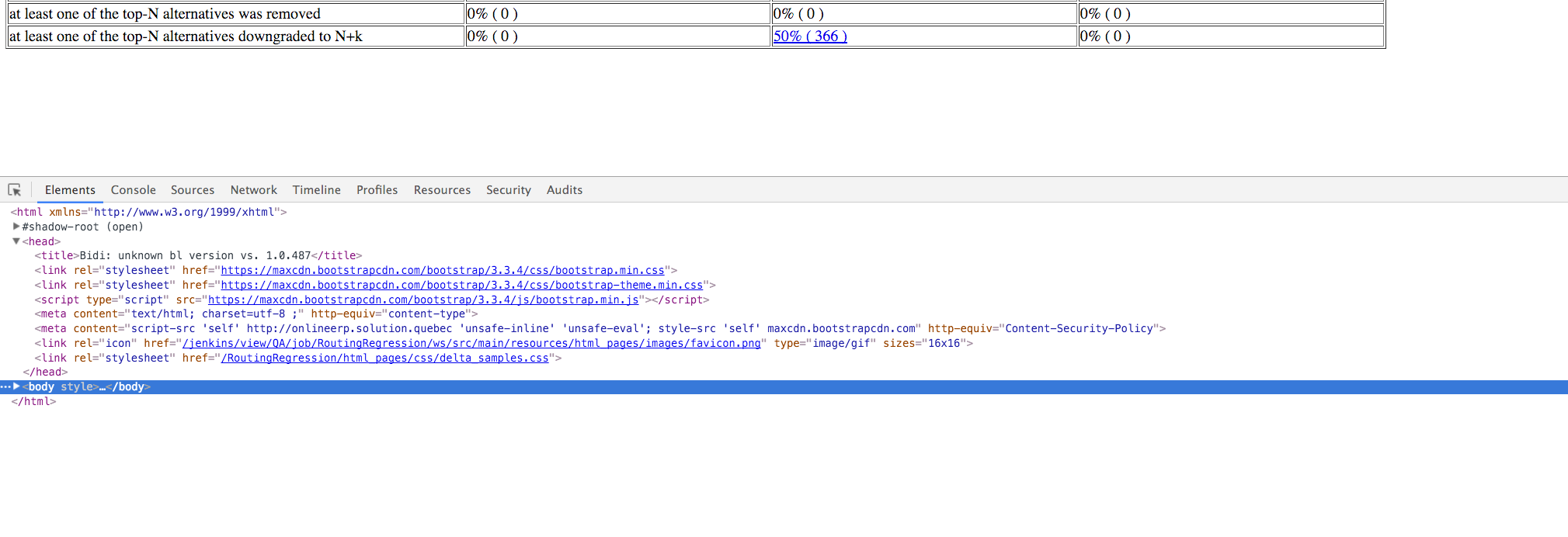
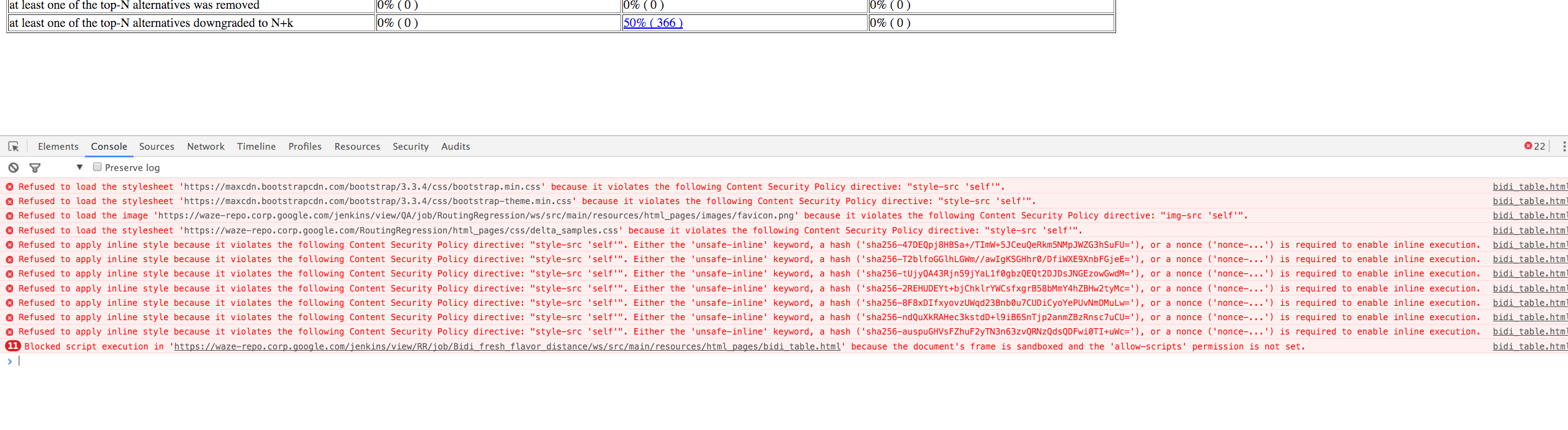
When I open the page in the browser (hosted on a Jenkins server) I see no css.
These are the errors (security policy)
I have seen some posts on stockoverflow, saying the <meta> should be like:
<meta http-equiv="content-type" content="text/html; charset=utf-8 ;">
<meta http-equiv="Content-Security-Policy" content="script-src 'self' http://onlineerp.solution.quebec 'unsafe-inline' 'unsafe-eval'; style-src 'self' maxcdn.bootstrapcdn.com">
but as you can see in my print screen that didn't help
any idea, how can I fix this?