I am trying to create a workflow to deploy Nuget packages to Github Package Repository using Github Actions.
In this case,
- The repository is inside an organization
- I am the owner of that organization
- I have admin access to the repository
- The repository has secrets listed
- The commit is mine
- The commit is a direct commit to a branch
But the action CANNOT access the secrets
Below is the workflow I am trying to execute
name: Build and Publish
on:
push:
branches:
- gh-packages
jobs:
build_and_publish:
env:
ACCESS_TOKEN: ${{ secrets.GITHUB_TOKEN }}
name: Publish Packages to NuGet
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v2
- uses: actions/setup-dotnet@v1
with:
dotnet-version: "3.0.100"
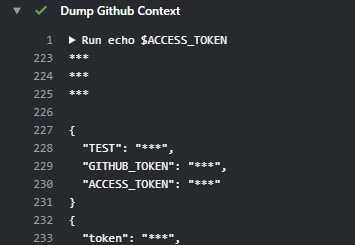
- name: Dump Github Context
env:
CONTEXT: ${{ toJson(github) }}
SECRETS: ${{ toJson(secrets) }}
TOK: ${{ secrets.ACCESS_TOKEN }}
TEST: ${{ secrets.TEST }
run: |
echo $ACCESS_TOKEN
echo $TOK
echo $TEST
echo $GITHUB_TOKEN
echo "$SECRETS"
echo "$CONTEXT"
- name: Setup Config
run: sed "s/ACCESS_TOKEN/$ACCESS_TOKEN/g" .nuget.config > nuget.config
- run: cat nuget.config
- name: Build
run: dotnet build -c Release
- name: Publish
run: chmod +x ./push.sh && ./push.sh
Both GITHUB_TOKEN and custom secrets like ACCESS_TOKEN are not working.
addition 01:
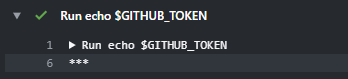
Even when setting the environment variable name as GITHUB_TOKEN doesn't seam to be working
name: Build and Publish
env:
GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
...