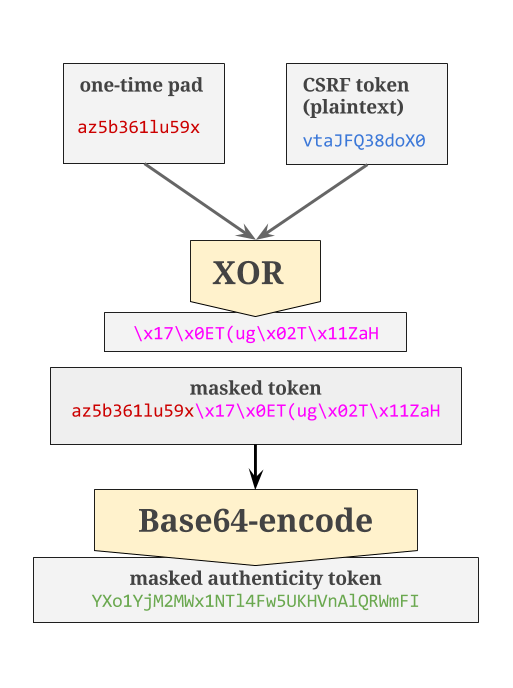
After reading about how the CSRF protection works in Rails, I tried to trigger CSRF protection by doing this:
Note: We are using cookie based sessions.
- Visit login page. Check CSRF token in meta => abc123
- Open a 2nd browser tab, and visit the same login page. CSRF token in meta is different => def456
- Go back to 1st tab.
- Submit login credentials.
I expected this to fail, because the 2nd tab generated a new, different CSRF token. When the login form submits, shouldn't the token that gets submitted to the server be an old, stale one?
However, this does work:
- Visit login page. Check CSRF token in meta => abc123
- Open a 2nd browser tab, and visit the same login page. CSRF token in meta is different => def456
- Go back to 1st tab.
- Submit login credentials.
- Logout (clearing session)
- Go to 2nd tab, and submit login.
In this case, I get an InvalidAuthenticityToken exception as expected. Why?