I have a question that (hopefully) someone can shed some light on. I was writing a Powershell script that would import a certificate to the Local Machine store, and assign the Everyone group Read permissions to the private key's on the certificate.
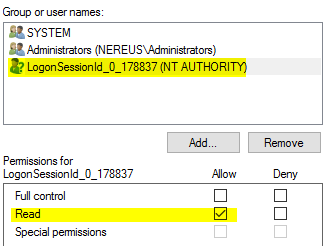
Now, I do have a working script that does accomplish this, but I've noticed that I have an account called "LogonSessionId_0_some-random-number" assigned Read permissions to the ACL on the private keys as shown in the following image:
At first I thought this was my script maybe doing this, but when I manually import the certificate I get the same result.
Has anyone seen this before or know why this is happening? What exactly is this account and why are permissions being assigned? I've tried to search for some answers on this but have come up short.
Not sure if it helps, but this is the portion of my code that imports the certificate and assigns the permissions:
$sslCert = gci Cert:\LocalMachine\My | WHERE {$_.Subject -match $getCerts}
$sslCertPrivKey = $sslCert.PrivateKey
$privKeyCertFile = Get-Item -path "$ENV:ProgramData\Microsoft\Crypto\RSA\MachineKeys\*" | WHERE {$_.Name -eq $sslCertPrivKey.CspKeyContainerInfo.UniqueKeyContainerName}
$privKeyAcl = (Get-Item -Path $privKeyCertFile.FullName).GetAccessControl("Access")
$permission = "Everyone","Read","Allow"
$accessRule = New-Object System.Security.AccessControl.FileSystemAccessRule $permission
$privKeyAcl.AddAccessRule($accessRule)
Set-Acl $privKeyCertFile.FullName $privKeyAcl
I'm using Windows 10 Pro.
Any help/insight is greatly appreciated!

wmiccommands (e.g.wmic useraccount where name='LogonSessionId_0_401541' get sid), but all experiments lead only to something likeNo Instance(s) Available.(Unimportant detail: I need that user's SID because I have to replace that user in the ACLs in a large file tree). – Cupid