How do you manage your Private / Public Keys for signing / validating JWTs in Spring Cloud environment?
The "problem":
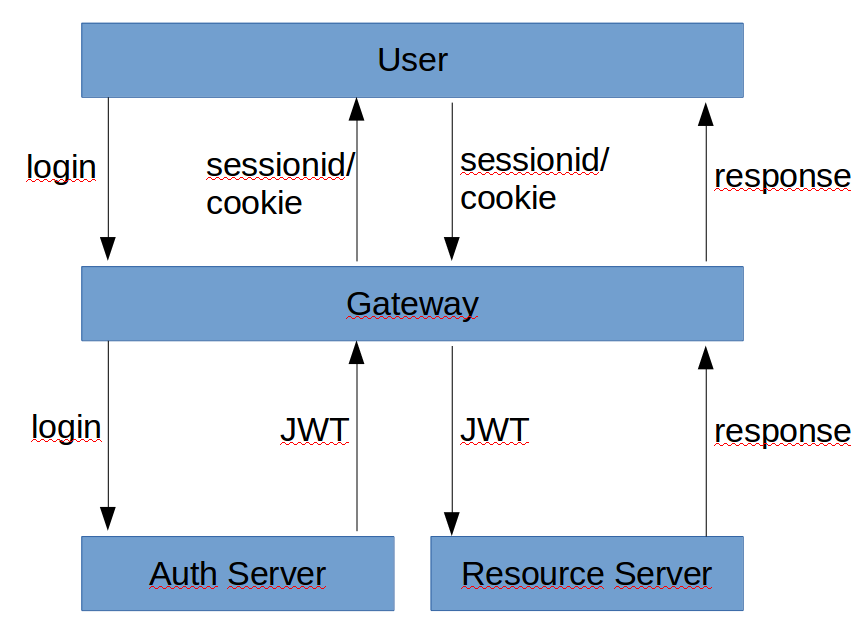
At the moment I generate a Key Pair. Then copy Private + Public Key to my auth-server application. And also copy the Public Key to each and every Resource Server.
When I now want to implement "Key Rotation" I have to somehow populate the new keys to every service.
The idea:
Maybe I could use the spring-cloud-config-server to store and distribute the Key Pairs?
The config server already provides database login credentials. So why not store even more sensitive information there?
Question(s):
If this is the way to go: How would you implement the key pair distribution with spring-cloud-config-server?
Do you have any security concerns?
How did you solve this problem? I guess there are better solutions.
EDIT:
Maybe there's some solution using Spring Oauth's security.oauth2.resource.jwt.keyUri property for JWKs?

...My problem isn't "securing the Private / Public Keys". The problem is more like "distributing a public key to my services". My auth service should generate a new key pair every 24 hours, which it uses to sign the JWT and then it somehow needs to publish the new public key to all other services (or just publish it to config server, and all other services will retrieve it from there). – Topazolite... EDIT:Should be enough to keep the public key. The private key can be thrown away each rotation. – Topazolite