This request was working a couple of months ago but when we tried again and directly using curl. It now returns an invalid_grant. I been trying to search the documentation, but only see the following words without any exact reasons why?
invalid_grant
- Refresh token has been revoked.
- Authorization code has been consumed already or does not exist.
The client settings is as follows.
curl -X POST https://test-sso.auth.amazoncognito.com/oauth2/token \
-H "Content-Type: application/x-www-form-urlencoded" \
-d "grant_type=authorization_code&client_id=xxxxxxx&redirect_uri=https%3A%2F%2F1c2d5a1xxxx.ngrok.io&code=SjkkDSSDs-b2A7nJPi3cmItyRZU4-b3GMjLls&code_verifier=sdXXXXXbUR2RmFIaTVQaVpTdndLOWoxOFU9Ig"
Has someone experienced this lately or has resolved this issue? I realized, even removing the PKCE. It's still returns invalid_grant.
Many thanks

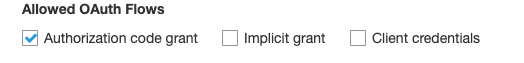
Authorization Code grantis enabled on the client ? – Indicative