I have created my Azure SQL server through ARM templates. To enable the vulnerability assessment I need to enable Advanced data security. I use the following code in my ARM template inside the resource bracket of the SQL server resource to enable this.
{
"name": "vulnerabilityAssessments",
"type": "vulnerabilityAssessments",
"apiVersion": "2018-06-01-preview",
"dependsOn": [
"[concat('Microsoft.Sql/servers/', parameters('sqlServerName'))]"
],
"properties": {
"storageContainerPath": "[concat('https://', parameters('storageAccountName'), '.blob.core.windows.net/vulnerability-assessment/')]",
"storageAccountAccessKey": "[listKeys(resourceId('Microsoft.Storage/storageAccounts', parameters('storageAccountName')), providers('Microsoft.Storage', 'storageAccounts').apiVersions[0]).keys[0].value]",
"recurringScans": {
"isEnabled": true,
"emailSubscriptionAdmins": false,
"emails": "[parameters('emailaddresses')]"
}
}
},
As you can see I set my storage account to the vulnerability assessment, but when i deploy this I get the following error:
VulnerabilityAssessmentADSIsDisabled", "message": "Advanced Data Security should be enabled in order to use Vulnerability Assessment."
And when I look into my advanced data security blade of the SQL server I see this been set:
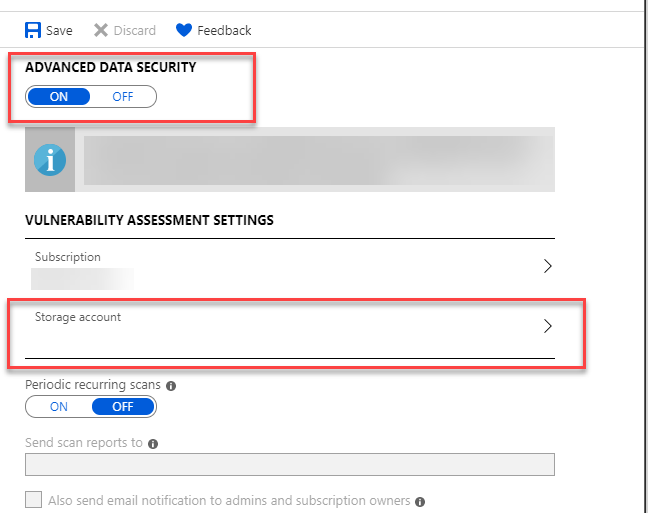
If I set the storage account manually. The vulnerability assessment is enabled.... I tried to change the vulnerability assessment brackets on the database level and tried to debug the storage account reference in the properties but can't seem to see what i do wrong or what I keep forgetting ? Is there anyone who tried to do this already ?
PS: Like you can see in the image periodic recurring scans is off whilst I have enabled this inside the recurring scans array of vulnerability assessment.
