I am trying to run GitLab's job using their shared Runners,
I've created a .gitlab-ci.yml and kept it at my project's root,
Configured AWS creds as the environment variables -
AWS_ACCESS_KEY_ID
AWS_SECRET_ACCESS_KEY
AWS_DEFAULT_REGION
under Settings -> CI / CD -> Variables
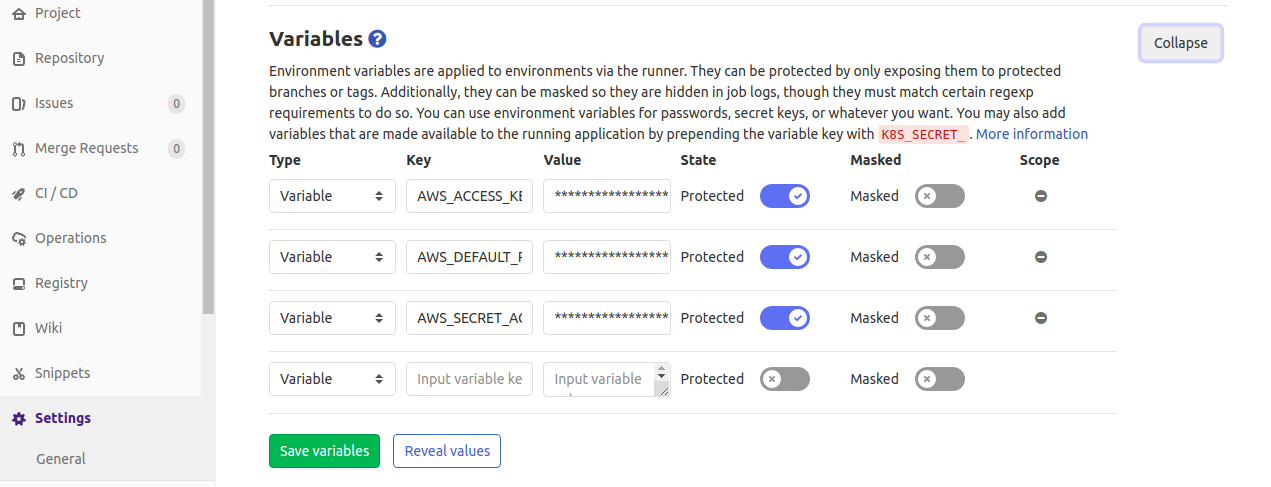
Double checked the branch I've trying to build from is protected
Following is my .gitlab-ci.yml -
stages:
- build
build:
image: python:latest
stage: build
script:
- apt-get update
- apt-get install -y zip unzip
- pip install awscli
- mkdir ~/.aws/
- touch ~/.aws/credentials
- pip install awscli
- printf "[eb-cli]\naws_access_key_id = %s\naws_secret_access_key = %s\nregion = %s\n" "$AWS_ACCESS_KEY_ID" "$AWS_SECRET_ACCESS_KEY" "$AWS_DEFAULT_REGION" >> ~/.aws/credentials
- bash cicdScript.sh
CICD script has the aws command -
$(aws s3 ls)
But I still get the following error -
Unable to locate credentials. You can configure credentials by running "aws configure".
Reference -
https://medium.com/faun/continuous-static-upload-to-aws-s3-using-gitlab-runners-17f0260a5af2

awscommand. Whichimageare you using for this? Can you post your.gitlab-ci.yml? – Vesuvius[eb-cli]in thecredentialsfile, maybe try using[default]instead? Although it's unsecure, what happens when you trycat ~/.aws/credentialsafter theprintf? (do revoke your keys after this though if it does work...) – Vesuvius