On the affected computer you can try to run an analysis with AzDO TLS 1.2-transition readiness checker: https://github.com/microsoft/azure-devops-tls12/blob/main/AzureDevOpsTls12Analysis.ps1
The script checks if the client TLS 1.2 usage is enabled, checks cipher suite issues and checks presence of switches needed to make legacy .NET Framework apps favor TLS 1.2. Based on findings it prints mitigation suggestions or generates tailored mitigation script (ps1).
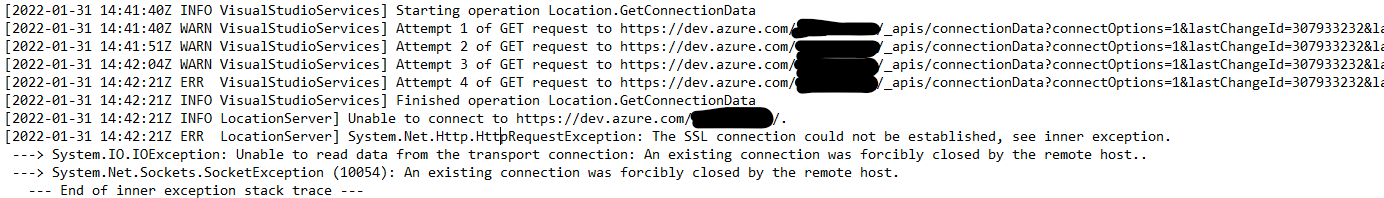
Simulating the issue described in the question, the script gives suggestion:
MITIGATION 'gpeditREM': via Local Group Policy setting
Run gpedit.msc:
- Navigate to "Computer Config/Administrative Templates/Network/SSL Config Settings"
- Choose setting "SSL Cipher Suite Order" -> Edit
- If 'Enabled' is not checked, then continue to the next mitigation below.
- If 'Enabled' is checked:
- *either* change to 'Not configured' (resets to OS-default setting)"
- *or* keep 'Enabled' and in field 'SSL Cipher Suites' add at least one of the following items to comma-separated list:
TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
- Press 'OK' button
Restart the computer
MITIGATION 'regFunctionsDEL': deletion of cipher suite list in registry
Mitigation script generated at .\Mitigation-regFunctionsDEL.ps1
Run the mitigation script as Administrator:
- If 'Done!' is printed, then operation was successfull.
- If 'Mitigation was not effective!' is printed, then cipher suites are enforced via domain GPO - talk to your domain administrator.
Screenshot: TLS 1.2-transition readiness checker on WS 2012 R2
Windows Server 2012 R2 (and older) are vulnerable to cipher suite problems because it supports only two out of four TLS 1.2 cipher suites currently required by AzDevOps (even those two are supported only if this update is applied).
Keep in mind Azure DevOps rolled-back its January 31st TLS 1.0/1.1 deprecation (except for IPv6 endpoints). Full deprecation is currently scheduled not sooner than on March 31st 2022 (announcement)
- Update (May 2022): Azure DevOps team has completed TLS 1.0/1.1 deprecation on dev.azure.com domain. Subdomains *.visualstudio.com will follow.
- Update (August 2022): Azure DevOps has started TLS 1.0/1.1 deprecation on *.visualstudio.com.
- Update (October 2022): Azure DevOps declared TLS 1.0/1.1 deprecation finished throughout all domains.
Update (January 2023): Azure DevOps endpoints changed list of cipher suites they support. Removed TLS_DHE_* ciphers, added two ECDHE+CBC ciphers. This may cause issues on Win Server 2012 R2 machines which have ECDHE+CBC disabled. <-- this has been reverted on February 02 2023