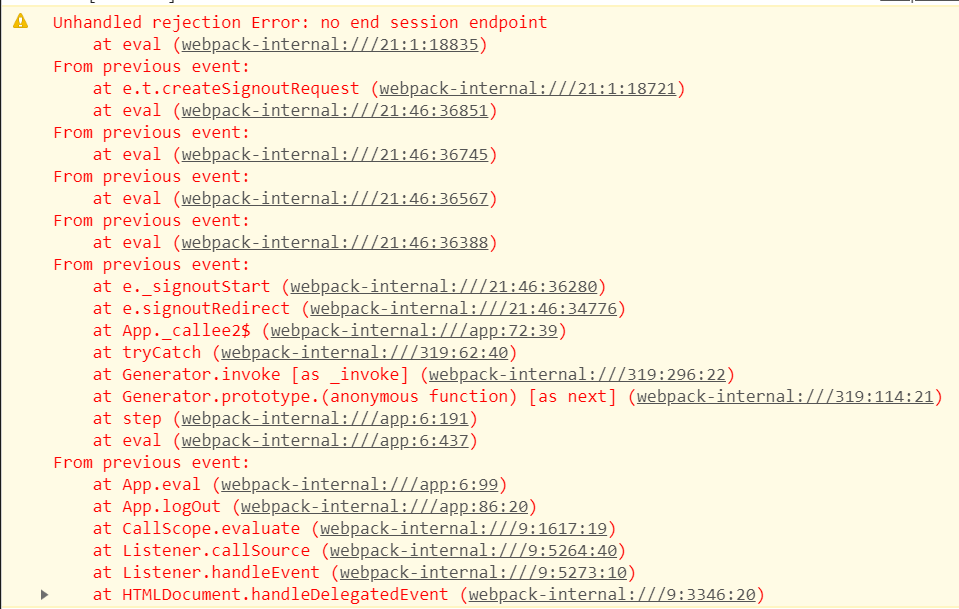
I've successfully used the oidc-client-js library by Brock Allen to authenticate my SPA app with Auth0 acting as my Identity Provider. However, when I try to use the library to sign the user out mgr.signoutRedirect({state: "my test"}), I receive an error: no end session endpoint.
A look at the metadata endpoint shows that there is a revocation endpoint.
I've configured the oidc-client-js library like so:
var settings = {
authority: 'https://susqsofttest.auth0.com/.well-known/openid-configuration',
client_id: 'my client id',
redirect_uri: 'http://localhost:8080/signin-oidc',
post_logout_redirect_uri: 'http://localhost:8080/logout',
response_type: 'id_token token',
scope: 'openid profile email',
revokeAccessTokenOnSignout: true,
automaticSilentRenew: true,
filterProtocolClaims: true,
loadUserInfo: true
};
var mgr = new UserManager(settings);
Any ideas of what I'm missing?