I'm making an app that needs to access the content of a Office 365 Calendar. That app shouldn't need a direct user action to log in and retreive its data, so I can't use a standard OAuth way to get this token.
I was a bit familiar of google's calendar way to do that, with it's "Service Account" logic, involving a non symetrical RSA key to do it, so I tried to find something like that for O365.
I've found this blog : https://blogs.msdn.microsoft.com/arsen/2015/09/18/certificate-based-auth-with-azure-service-principals-from-linux-command-line/ that helped me a lot configuring an application and setting up all the keys on both side to allow the connection. In the end, I managed to make it work, got a token and list the resourcegroups.
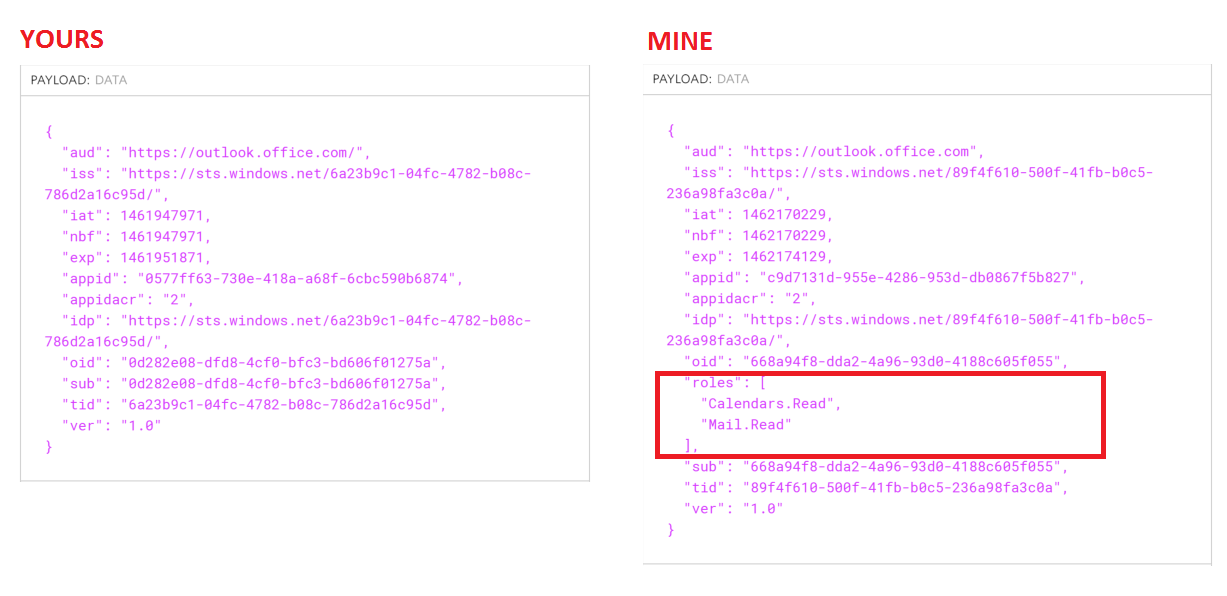
All was fine and I exepected it to work quite easily with Microsoft graph API. So : - I added the Microsft Graph API in my application's Authorizations on Azure Management and added all the read / write permissions on all users' calendars ( in the application's authorizations and in delegated authorization ) - I regenerated the tokens so the new rights can be added to it - I used this token to get a list of the calendars
And it never worked. I have the token, and the request gives me the good scopes with it. So I know i'm on the right app, and everything. When i give the token to outlook.office.com, I have this message : <>
I've probably missed a step somewhere, but I can't find where. In my requests ? In my Azure account ?
Any help please ?
The requests (didn't blur anything, just a test account anyway).
Get Token Request :
POST /6a23b9c1-04fc-4782-b08c-786d2a16c95d/oauth2/token HTTP/1.1
Host: login.microsoftonline.com
Content-Type: application/x-www-form-urlencoded
Cache-Control: no-cache
Postman-Token: f7b2884d-44e9-c48a-6245-453be490758c
grant_type=client_credentials&client_id=0577ff63-730e-418a-a68f-6cbc590b6874&resource=https%3A%2F%2Foutlook.office.com%2F&client_assertion_type=urn%3Aietf%3Aparams%3Aoauth%3Aclient-assertion-type%3Ajwt-bearer&client_assertion=eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCIsIng1dCI6ImxhVkMzbEd3K3hKWkpkTUQrbUpmdmRoU1V2bz0ifQ.eyJhdWQiOiJodHRwczovL2xvZ2luLm1pY3Jvc29mdG9ubGluZS5jb20vNmEyM2I5YzEtMDRmYy00NzgyLWIwOGMtNzg2ZDJhMTZjOTVkL29hdXRoMi90b2tlbiIsImlzcyI6IjA1NzdmZjYzLTczMGUtNDE4YS1hNjhmLTZjYmM1OTBiNjg3NCIsInN1YiI6IjA1NzdmZjYzLTczMGUtNDE4YS1hNjhmLTZjYmM1OTBiNjg3NCIsImp0aSI6IjAuMTgyOTg1ODUzNjM2NjM3MzMiLCJuYmYiOiIxNDYxOTQyODU2IiwiZXhwIjoiMTUyMjQyMzg1NiIsImlhdCI6MTQ2MTk0Mzg1Nn0.Czm9ks_jrEVViUDjfMF1uVUlf5sZrCSGtCmisFn3c8119KQ-OczLpWbpU3crJjidiP2y-xcSGjRSCGYJPiwq2Qks45_97-jBe_fBPoJb5lni5QYT_2ep6OyaAnId4VxlF9WScxFfHEtLqOsqOZwB4c6_YXdOiy82SJ0sLqLgZrFlnqYn6uMXGWThEFKPR3qsolgO4Wn5lthFRwF__IuIpg2DnjyNIz2KVhqVLqqZ-pglzE_soaKldiAR4bAZMxlndhMCnoUADgfsR0PAaZ-AyM0me4K7FrGbLpaTdXU6M4v9edLM9J23dg82HOKdf0GDC6pCIxKmIsuTR8IxGfxoTw
Get Token Answer :
{
"token_type" : "Bearer",
"scope" : "Calendars.Read Calendars.ReadWrite",
"expires_in" : "3600",
"expires_on" : "1461951871",
"not_before" : "1461947971",
"resource" : "https://outlook.office.com/",
"access_token" : "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsIng1dCI6Ik1uQ19WWmNBVGZNNXBPWWlKSE1iYTlnb0VLWSIsImtpZCI6Ik1uQ19WWmNBVGZNNXBPWWlKSE1iYTlnb0VLWSJ9.eyJhdWQiOiJodHRwczovL291dGxvb2sub2ZmaWNlLmNvbS8iLCJpc3MiOiJodHRwczovL3N0cy53aW5kb3dzLm5ldC82YTIzYjljMS0wNGZjLTQ3ODItYjA4Yy03ODZkMmExNmM5NWQvIiwiaWF0IjoxNDYxOTQ3OTcxLCJuYmYiOjE0NjE5NDc5NzEsImV4cCI6MTQ2MTk1MTg3MSwiYXBwaWQiOiIwNTc3ZmY2My03MzBlLTQxOGEtYTY4Zi02Y2JjNTkwYjY4NzQiLCJhcHBpZGFjciI6IjIiLCJpZHAiOiJodHRwczovL3N0cy53aW5kb3dzLm5ldC82YTIzYjljMS0wNGZjLTQ3ODItYjA4Yy03ODZkMmExNmM5NWQvIiwib2lkIjoiMGQyODJlMDgtZGZkOC00Y2YwLWJmYzMtYmQ2MDZmMDEyNzVhIiwic3ViIjoiMGQyODJlMDgtZGZkOC00Y2YwLWJmYzMtYmQ2MDZmMDEyNzVhIiwidGlkIjoiNmEyM2I5YzEtMDRmYy00NzgyLWIwOGMtNzg2ZDJhMTZjOTVkIiwidmVyIjoiMS4wIn0.L8mP4t_Zmxfl5vJQwEaOsd-ere81jtz9ltzxk0TA0qA_hwRIYNVmHrydyPTHHQC7Jv3M6hiSnSVyVeXX_uYNFkPRZ3Sy_XOjmOF5xslMrw1niqE6J7OhQ5PEPmOfa0mQoWManChemDV5JCdxNOotBd4xes_jzg9tLMihzpqBcAUo3zGn8q5PT7AG-pydOEaHCWwDSKlHlFkBjZ3y_NTtQadDSR9aE2H6DOtP5-hXCpHqzkZODTZCuSBQRz1vCshcd8kZiuX_ebxItlJ8JU-zUr1YJFy9jww0NtROOB71xJP9IUf2NjMS-rQvR2qL8vfLPTArpgQFRU9cCZ4KpbVs3Q"
}
Calendar List Request :
GET /api/v2.0/me/calendars HTTP/1.1
Host: outlook.office.com
Authorization: Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsIng1dCI6Ik1uQ19WWmNBVGZNNXBPWWlKSE1iYTlnb0VLWSIsImtpZCI6Ik1uQ19WWmNBVGZNNXBPWWlKSE1iYTlnb0VLWSJ9.eyJhdWQiOiJodHRwczovL291dGxvb2sub2ZmaWNlLmNvbS8iLCJpc3MiOiJodHRwczovL3N0cy53aW5kb3dzLm5ldC82YTIzYjljMS0wNGZjLTQ3ODItYjA4Yy03ODZkMmExNmM5NWQvIiwiaWF0IjoxNDYxOTQ3OTcxLCJuYmYiOjE0NjE5NDc5NzEsImV4cCI6MTQ2MTk1MTg3MSwiYXBwaWQiOiIwNTc3ZmY2My03MzBlLTQxOGEtYTY4Zi02Y2JjNTkwYjY4NzQiLCJhcHBpZGFjciI6IjIiLCJpZHAiOiJodHRwczovL3N0cy53aW5kb3dzLm5ldC82YTIzYjljMS0wNGZjLTQ3ODItYjA4Yy03ODZkMmExNmM5NWQvIiwib2lkIjoiMGQyODJlMDgtZGZkOC00Y2YwLWJmYzMtYmQ2MDZmMDEyNzVhIiwic3ViIjoiMGQyODJlMDgtZGZkOC00Y2YwLWJmYzMtYmQ2MDZmMDEyNzVhIiwidGlkIjoiNmEyM2I5YzEtMDRmYy00NzgyLWIwOGMtNzg2ZDJhMTZjOTVkIiwidmVyIjoiMS4wIn0.L8mP4t_Zmxfl5vJQwEaOsd-ere81jtz9ltzxk0TA0qA_hwRIYNVmHrydyPTHHQC7Jv3M6hiSnSVyVeXX_uYNFkPRZ3Sy_XOjmOF5xslMrw1niqE6J7OhQ5PEPmOfa0mQoWManChemDV5JCdxNOotBd4xes_jzg9tLMihzpqBcAUo3zGn8q5PT7AG-pydOEaHCWwDSKlHlFkBjZ3y_NTtQadDSR9aE2H6DOtP5-hXCpHqzkZODTZCuSBQRz1vCshcd8kZiuX_ebxItlJ8JU-zUr1YJFy9jww0NtROOB71xJP9IUf2NjMS-rQvR2qL8vfLPTArpgQFRU9cCZ4KpbVs3Q
Cache-Control: no-cache
Postman-Token: e85ac526-c56a-4d5b-2f74-83f4033decb4
Answer empty, but in the headers :
Content-Length →0
Date →Fri, 29 Apr 2016 16:44:59 GMT
Server →Microsoft-IIS/8.5
WWW-Authenticate →Bearer client_id="00000002-0000-0ff1-ce00-000000000000", trusted_issuers="00000001-0000-0000-c000-000000000000@*", token_types="app_asserted_user_v1 service_asserted_app_v1", authorization_uri="https://login.windows.net/common/oauth2/authorize", error="invalid_token",Basic Realm="",Basic Realm=""
X-BEServer →VI1PR08MB0910
X-BackEndHttpStatus →401
X-CalculatedBETarget →VI1PR08MB0910.eurprd08.prod.outlook.com
X-DiagInfo →VI1PR08MB0910
X-FEServer →AM3PR08CA0034
X-MSEdge-Ref →Ref A: B612166BB1764A45B0F3BCE6DF9CB639 Ref B: A8D71806CB57091B57FD0130AABF9D85 Ref C: Fri Apr 29 09:45:00 2016 PST
X-Powered-By →ASP.NET
request-id →26f132ca-df5e-439f-bd4f-7d655ba7df21
x-ms-diagnostics →2000008;reason="The token contains no permissions, or permissions can not be understood.";error_category="invalid_grant"