How do I find out which process is listening on a TCP or UDP port on Windows?
PowerShell
TCP
Get-Process -Id (Get-NetTCPConnection -LocalPort YourPortNumberHere).OwningProcess
UDP
Get-Process -Id (Get-NetUDPEndpoint -LocalPort YourPortNumberHere).OwningProcess
cmd
netstat -a -b
(Add -n to stop it trying to resolve hostnames, which will make it a lot faster.)
Note Dane's recommendation for TCPView. It looks very useful!
-a Displays all connections and listening ports.
-b Displays the executable involved in creating each connection or listening port. In some cases well-known executables host multiple independent components, and in these cases the sequence of components involved in creating the connection or listening port is displayed. In this case the executable name is in [] at the bottom, on top is the component it called, and so forth until TCP/IP was reached. Note that this option can be time-consuming and will fail unless you have sufficient permissions.
-n Displays addresses and port numbers in numerical form.
-o Displays the owning process ID associated with each connection.
netstat -a -n -p. The -b and -d options are not available. The -o option was for timers. The -p options displayed the program name and PID. (on debian 8). –
Alkyne 1234 - then you can use tasklist /fi "pid eq 1234" to find out the name and other details of the process. –
Quoits netsh http show urlacl. It shows system URL reservations. –
Elbrus | grep :80 is useful for search for specific port. if installed grep. –
Phrygian netsh int ipv4 show excludedportrange protocol=tcp –
Albuminous Resource Monitor is the only one with accurate results (at least on Windows 11 ). –
Booher There's a native GUI for Windows:
Start menu → All Programs → Accessories → System Tools → Resource Monitor
or run
resmon.exe,or from TaskManager → Performance tab.

Open Resource Monitor button. From run prompt perfmon /res command also works to open resource monitor. –
Checkrein For Windows:
netstat -aon | find /i "listening"
netstat -aon | find /i "abhören" for german. –
Jaws FIND: Parameter format not correct –
Ballinger Use TCPView if you want a GUI for this. It's the old Sysinternals application that Microsoft bought out.
The -b switch mentioned in most answers requires you to have administrative privileges on the machine. You don't really need elevated rights to get the process name!
Find the pid of the process running in the port number (e.g., 8080)
netstat -ano | findStr "8080"
Find the process name by pid
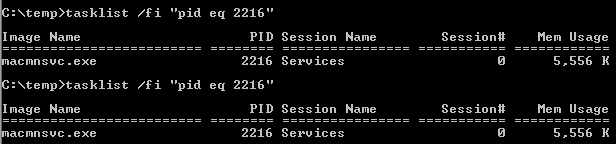
tasklist /fi "pid eq 2216"
You can get more information if you run the following command:
netstat -aon | find /i "listening" |find "port"
using the 'Find' command allows you to filter the results. find /i "listening" will display only ports that are 'Listening'. Note, you need the /i to ignore case, otherwise you would type find "LISTENING". | find "port" will limit the results to only those containing the specific port number. Note, on this it will also filter in results that have the port number anywhere in the response string.
FIND: Parameter format not correct. You need to add a space after the find criteria. This will leave you with netstat -aon | find /i "listening" | find "1234 ". –
Vanda {back tick}"listening{back tick}"" |find "{back tick}"port{back tick}"" (<- note the escaped quotes - excuse the term back tick as i cannot add the actual character as it thinks its a snipping) –
Handcuff Open a command prompt window (as Administrator) From "Start\Search box" Enter "cmd" then right-click on "cmd.exe" and select "Run as Administrator"
Enter the following text then hit Enter.
netstat -abno-a Displays all connections and listening ports.
-b Displays the executable involved in creating each connection or listening port. In some cases well-known executables host multiple independent components, and in these cases the sequence of components involved in creating the connection or listening port is displayed. In this case the executable name is in [] at the bottom, on top is the component it called, and so forth until TCP/IP was reached. Note that this option can be time-consuming and will fail unless you have sufficient permissions.
-n Displays addresses and port numbers in numerical form.
-o Displays the owning process ID associated with each connection.
Find the Port that you are listening on under "Local Address"
Look at the process name directly under that.
NOTE: To find the process under Task Manager
Note the PID (process identifier) next to the port you are looking at.
Open Windows Task Manager.
Select the Processes tab.
Look for the PID you noted when you did the netstat in step 1.
If you don’t see a PID column, click on View / Select Columns. Select PID.
Make sure “Show processes from all users” is selected.
Get PID and Image Name
Use only one command:
for /f "tokens=5" %a in ('netstat -aon ^| findstr 9000') do tasklist /FI "PID eq %a"
where 9000 should be replaced by your port number.
The output will contain something like this:
Image Name PID Session Name Session# Mem Usage
========================= ======== ================ =========== ============
java.exe 5312 Services 0 130,768 K
Explanation:
it iterates through every line from the output of the following command:
netstat -aon | findstr 9000from every line, the PID (
%a- the name is not important here) is extracted (PID is the5th element in that line) and passed to the following commandtasklist /FI "PID eq 5312"
If you want to skip the header and the return of the command prompt, you can use:
echo off & (for /f "tokens=5" %a in ('netstat -aon ^| findstr 9000') do tasklist /NH /FI "PID eq %a") & echo on
Output:
java.exe 5312 Services 0 130,768 K
findstr :9000 if not,you would even find apps what contain the number (e.g. when you search "80" you would find apps on port 80, 800, 8000 too). –
Lifeordeath First we find the process id of that particular task which we need to eliminate in order to get the port free:
Type
netstat -n -a -o
After executing this command in the Windows command line prompt (cmd), select the pid which I think the last column. Suppose this is 3312.
Now type
taskkill /F /PID 3312
You can now cross check by typing the netstat command.
NOTE: sometimes Windows doesn’t allow you to run this command directly on CMD, so first you need to go with these steps:
From the start menu -> command prompt (right click on command prompt, and run as administrator)
taskkill -F -PID 3312 –
Ptero With PowerShell 5 on Windows 10 or Windows Server 2016, run the Get-NetTCPConnection cmdlet. I guess that it should also work on older Windows versions.
The default output of Get-NetTCPConnection does not include Process ID for some reason and it is a bit confusing. However, you could always get it by formatting the output. The property you are looking for is OwningProcess.
If you want to find out the ID of the process that is listening on port 443, run this command:
PS C:\> Get-NetTCPConnection -LocalPort 443 | Format-List LocalAddress : :: LocalPort : 443 RemoteAddress : :: RemotePort : 0 State : Listen AppliedSetting : OwningProcess : 4572 CreationTime : 02.11.2016 21:55:43 OffloadState : InHostFormat the output to a table with the properties you look for:
PS C:\> Get-NetTCPConnection -LocalPort 443 | Format-Table -Property LocalAddress, LocalPort, State, OwningProcess LocalAddress LocalPort State OwningProcess ------------ --------- ----- ------------- :: 443 Listen 4572 0.0.0.0 443 Listen 4572If you want to find out a name of the process, run this command:
PS C:\> Get-Process -Id (Get-NetTCPConnection -LocalPort 443).OwningProcess Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName ------- ------ ----- ----- ------ -- -- ----------- 143 15 3448 11024 4572 0 VisualSVNServer
To get a list of all the owning process IDs associated with each connection:
netstat -ao |find /i "listening"
If want to kill any process have the ID and use this command, so that port becomes free
Taskkill /F /IM PID of a process
It is very simple to get the port number from a PID in Windows.
The following are the steps:
Go to run → type cmd → press Enter.
Write the following command...
netstat -aon | findstr [port number](Note: Don't include square brackets.)
Press Enter...
Then cmd will give you the detail of the service running on that port along with the PID.
Open Task Manager and hit the service tab and match the PID with that of the cmd, and that's it.
netstat -aof | findstr :8080 (Change 8080 for any port)
In case someone need an equivalent for macOS like I did, here is it:
lsof -i tcp:8080
After you get the PID of the process, you can kill it with:
kill -9 <PID>
To find out which specific process (PID) is using which port:
netstat -anon | findstr 1234
Where 1234 is the PID of your process. [Go to Task Manager → Services/Processes tab to find out the PID of your application.]
-n flag set twice. -ano is enough. –
Lonnie PowerShell
If you want to have a good overview, you can use this:
Get-NetTCPConnection -State Listen | Select-Object -Property *, `
@{'Name' = 'ProcessName';'Expression'={(Get-Process -Id $_.OwningProcess).Name}} `
| select ProcessName,LocalAddress,LocalPort
Then you get a table like this:
ProcessName LocalAddress LocalPort
----------- ------------ ---------
services :: 49755
jhi_service ::1 49673
svchost :: 135
services 0.0.0.0 49755
spoolsv 0.0.0.0 49672
For UDP, it is:
Get-NetUDPEndpoint | Select-Object -Property *, `
@{'Name' = 'ProcessName';'Expression'={(Get-Process -Id $_.OwningProcess).Name}} `
| select ProcessName,LocalAddress,LocalPort
Just open a command shell and type (saying your port is 123456):
netstat -a -n -o | find "123456"
You will see everything you need.
The headers are:
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:37 0.0.0.0:0 LISTENING 1111
This is as mentioned here.
findstr 123456 (without quotes) or find "123456" (with quotes). (@Josh) –
Gonsalez If you'd like to use a GUI tool to do this there's Sysinternals' TCPView.
Open the command prompt - start → Run →
cmd, or start menu → All Programs → Accessories → Command Prompt.Type
netstat -aon | findstr '[port_number]'
Replace the [port_number] with the actual port number that you want to check and hit Enter.
- If the port is being used by any application, then that application’s detail will be shown. The number, which is shown at the last column of the list, is the PID (process ID) of that application. Make note of this.
Type
tasklist | findstr '[PID]'
Replace the [PID] with the number from the above step and hit Enter.
- You’ll be shown the application name that is using your port number.
Netstat:
- -a displays all connection and listening ports
- -b displays executables
- -n stop resolve hostnames (numerical form)
-o owning process
netstat -bano | findstr "7002" netstat -ano > ano.txt
The Currports tool helps to search and filter
Type in the command: netstat -aon | findstr :DESIRED_PORT_NUMBER
For example, if I want to find port 80: netstat -aon | findstr :80
This answer was originally posted to this question.
netstat -ao and netstat -ab tell you the application, but if you're not a system administrator you'll get "The requested operation requires elevation".
It's not ideal, but if you use Sysinternals' Process Explorer you can go to specific processes' properties and look at the TCP tab to see if they're using the port you're interested in. It is a bit of a needle and haystack thing, but maybe it'll help someone...
Using Windows' default shell (PowerShell) and without external applications
For those using PowerShell, try Get-NetworkStatistics:
> Get-NetworkStatistics | where Localport -eq 8000
ComputerName : DESKTOP-JL59SC6
Protocol : TCP
LocalAddress : 0.0.0.0
LocalPort : 8000
RemoteAddress : 0.0.0.0
RemotePort : 0
State : LISTENING
ProcessName : node
PID : 11552
I recommend CurrPorts from NirSoft.
CurrPorts can filter the displayed results. TCPView doesn't have this feature.
Note: You can right click a process's socket connection and select "Close Selected TCP Connections" (You can also do this in TCPView). This often fixes connectivity issues I have with Outlook and Lync after I switch VPNs. With CurrPorts, you can also close connections from the command line with the "/close" parameter.
A single-line solution that helps me is this one. Just substitute 3000 with your port:
$P = Get-Process -Id (Get-NetTCPConnection -LocalPort 3000).OwningProcess; Stop-Process $P.Id
Edit: Changed kill to Stop-Process for more PowerShell-like language
Get-Process -Id (Get-NetTCPConnection -LocalPort 3000).OwningProcess | Stop-Process –
Hammurabi Follow these tools: From cmd: C:\> netstat -anob with Administrator privileges.
All from sysinternals.com.
If you just want to know process running and threads under each process, I recommend learning about wmic. It is a wonderful command-line tool, which gives you much more than you can know.
Example:
c:\> wmic process list brief /every:5
The above command will show an all process list in brief every 5 seconds. To know more, you can just go with /? command of windows , for example,
c:\> wmic /?
c:\> wmic process /?
c:\> wmic prcess list /?
And so on and so forth. :)
Use:
netstat -a -o
This shows the PID of the process running on a particular port.
Keep in mind the process ID and go to Task Manager and services or details tab and end the process which has the same PID.
Thus you can kill a process running on a particular port in Windows.
To find pid who using port 8000
netstat -aon | findstr '8000'
To Kill that Process in windows
taskkill /pid pid /f
where pid is the process id which you get form first command
You can also check the reserved ports with the command below. Hyper-V reserve some ports, for instance.
netsh int ipv4 show excludedportrange protocol=tcp
Programmatically, you need stuff from iphlpapi.h, for example GetTcpTable2(). Structures like MIB_TCP6ROW2 contain the owner PID.
Using PowerShell... ...this would be your friend (replace 8080 with your port number):
netstat -abno | Select-String -Context 0,1 -Pattern 8080
Sample output
> TCP 0.0.0.0:8080 0.0.0.0:0 LISTENING 2920
[tnslsnr.exe]
> TCP [::]:8080 [::]:0 LISTENING 2920
[tnslsnr.exe]
So in this example tnslsnr.exe (OracleXE database) is listening on port 8080.
Quick explanation
Select-Stringis used to filter the lengthy output ofnetstatfor the relevant lines.-Patterntests each line against a regular expression.-Context 0,1will output 0 leading lines and 1 trailing line for each pattern match.
For Windows, if you want to find stuff listening or connected to port 1234, execute the following at the cmd prompt:
netstat -na | find "1234"
Use the below batch script which takes a process name as an argument and gives netstat output for the process.
@echo off
set procName=%1
for /f "tokens=2 delims=," %%F in ('tasklist /nh /fi "imagename eq %1" /fo csv') do call :Foo %%~F
goto End
:Foo
set z=%1
echo netstat for : "%procName%" which had pid "%1"
echo ----------------------------------------------------------------------
netstat -ano |findstr %z%
goto :eof
:End
Based on answers with info and kill, for me it is useful to combine them in one command. And you can run this from cmd to get information about process that listen on given port (example 8080):
for /f "tokens=3 delims=LISTENING" %i in ('netstat -ano ^| findStr "8080" ^| findStr "["') do @tasklist /nh /fi "pid eq %i"
Or if you want to kill it:
for /f "tokens=3 delims=LISTENING" %i in ('netstat -ano ^| findStr "8080" ^| findStr "["') do @Taskkill /F /IM %i
You can also put those command into a bat file (they will be slightly different - replace %i for %%i):
File portInfo.bat
for /f "tokens=3 delims=LISTENING" %%i in (
'netstat -ano ^| findStr "%1" ^| findStr "["'
) do @tasklist /nh /fi "pid eq %%i"
File portKill.bat
for /f "tokens=3 delims=LISTENING" %%i in (
'netstat -ano ^| findStr "%1" ^| findStr "["'
) do @Taskkill /F /IM %%i
Then you from cmd you can do this:
portInfo.bat 8080
or
portKill.bat 8080
.\portInfo.bat 800 in PowerShell it give something like this: C:\work>for /F "tokens=3 delims=LISTENING" %i in ('netstat -ano | findStr "800" | findStr "["') do (tasklist /fi "pid eq %i" ) C:\work>(tasklist /fi "pid eq 4" ) Image Name PID Session Name Session# Mem Usage ========================= ======== ================ =========== ============ System 4 Services 0 1,820 K –
Cuttler portInfo.bat in a powershell terminal, then executed .\portInfo.bat 8080. The output was just the content of the batch file. Very well posslble I'm overlooking something. Note, I'm using PowerShell 6.2.3 on Windows 10. I also tried it in a regular command prompt, but the result was the same: Output of the content of the script. I'm sure I'm missing a crucial piece of information to make this work. –
Ratfink for /f "tokens=3 delims=LISTENING" %i in ('netstat -ano ^| findStr "8080" ^| findStr "["') do tasklist /fi "pid eq %i" –
Cuttler /nh : @tasklist /nh /fi "pid eq %i"? And precisely the door: Findstr ":8080" –
Lissa © 2022 - 2024 — McMap. All rights reserved.

netstat -aof | findstr :8080(Change 8080 for any port) – Crorenetstat -aof | findstr :3306to find the MySQL process on Windows 10 and works like a charm. – Crorenetstat -aof | grep :4200– Slumgullion