I have created an mvc site and I'm posting a large amount of json form data (Content-Type:application/x-www-form-urlencoded)
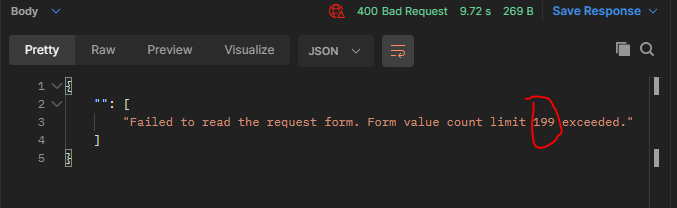
back to the mvc controller. When I do this, I receive a 500 response that states: "InvalidDataException: Form value count limit 1024 exceeded."
In previous versions of aspnet, you would add the following to the web.config to increase the limit:
<appSettings>
<add key="aspnet:MaxHttpCollectionKeys" value="5000" />
<add key="aspnet:MaxJsonDeserializerMembers" value="5000" />
</appSettings>
When I put these values in the web.config, I do not see any change, so I'm guessing Microsoft is no longer reading these values out of the web.config. However, I cannot figure out where these settings should be set.
Any help with increasing the form value count is greatly appreciated!
To be clear, this request works perfectly fine when the number of items in my post data is less than 1024.
Update: In asp.net MVC Core 3.1 the error message is - "Failed to read the request form. Form value count limit 1024 exceeded."

large amount of json form data? Are you posting data asapplication/x-www-form-urlencodedcontent type orapplication/json? – Banka