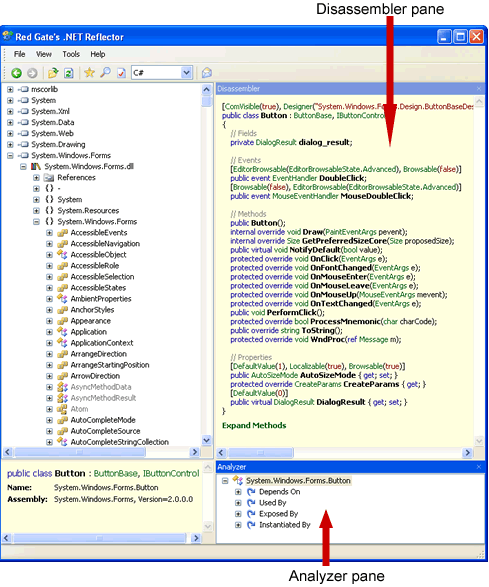
.NET compilation in general is pretty easy: to get a feel for this yourself, just grab a copy of .NET Reflector and give it a try.
In most cases, there will be no need to recompile the code in order to remove a simple license check: simply patching the MSIL will do the trick.
Protecting yourself against this scenario yields rapidly diminishing returns: there will always be someone clever enough to bypass whatever additional checks you add to your code. For example, you could add a digital signature to your code, and refuse to run of the signature doesn't match (indicating the code has been tampered with, for example to remove the license check).
The game then becomes to remove the signature check (in addition to the license key check). So you add another check, which can then be bypassed, et cetera, ad infinitum.
There's a whole industry of code obfuscatation and copy protection tools to help you defend your software against issues like this. It's up to you to decide if the additional effort on your side, and the annoyance you'll cause your legitimate customers, is worth buying into these solutions...