Edit (2017-05-02): Microsoft Network Monitor - has been replaced by Microsoft Message Analyzer - which serves the same purpose. See also comment below this answer or the answer further down for how to use it!
Note: Microsoft Message Analyzer was deprecated in late 2019, and is no longer available for download.
Original Answer
There is another much underrated tool from Microsoft itself: 'Microsoft Network Monitor'. Basically this is very similar to wireshark with the exception that some specific MS protocols have better parser and visualisation support than wireshark itself and obviously it would only run under windows ;-).
The tool is quite old and looks abandoned (havn't seen a newer release so far) but still does an good job and the grammar for defining new protocols is quite neat/interesting - so this still possess a lot of power for the future.
![mnm 3.4 about dialog]()
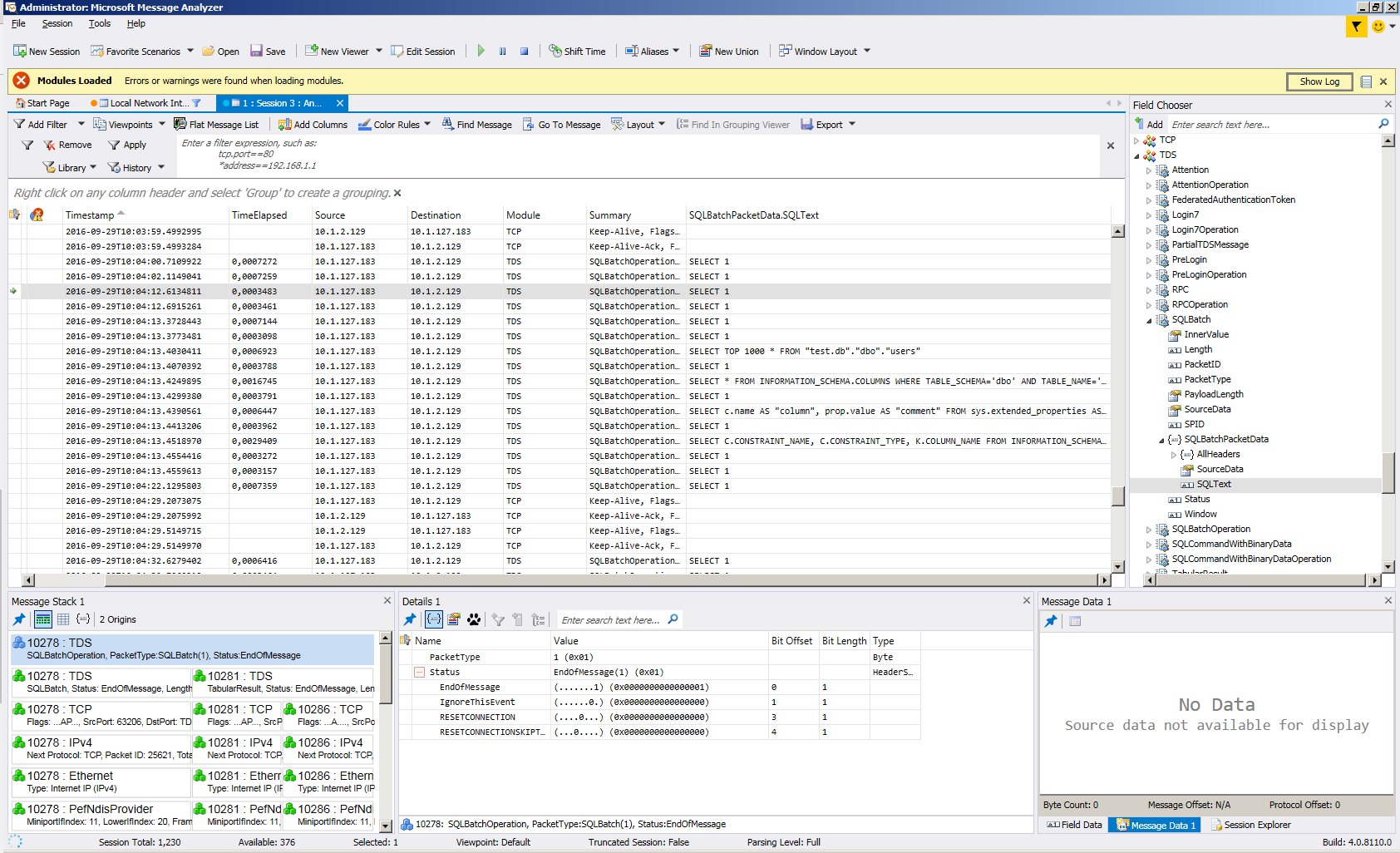
Analysis Example - Recording is filtered for TDS - so the other packets are discared mostly:
![Example Session for TDS (MSSQL)]()
This is also true for sql server connections. The MNM can even visualize the resultsets going over the wire - quite neat. Nonetheless wireshark as mentioned above would be sufficient to validate encryption and applied certificates on the wire itself. Means it can understand the TDS-Protocoll fully.
Handling TLS
Also with an extension (so called experts) 'NmDecrypt' and the right certificates (including private keys) - it is possible to decrypt protocolls - quite nice for TDS which uses TLS INSIDE of TDS - no wonder - no one has really implemented that yet as a fully supported protocoll for wireshark ;)
So far - regarding MSSQL-Traffic - or to be more precice TDS-Protocol this is the best tool I've come across so far. Wireshark is cool - but in this case MNM is 'better'. Have phun! ;)
Links for the tools: