App Service private certificate requirements
App Service private certificates must meet the following requirements:
- Exported as a password-protected PFX file, encrypted using triple DES.
- Contains private key at least 2048 bits long
- Contains all intermediate certificates and the root certificate in the certificate chain.
Option 1: Use legacy provider in OpenSSL 3+
OpenSSL 3+ no longer uses DES encryption as a default. The original command needs the -legacy and -provider-path (path to legacy.dll) arguments appended:
openssl pkcs12 -export -out domain.name.pfx -inkey domain.name.key -in domain.name.crt -legacy -provider-path 'C:\Program Files\OpenSSL-Win64\bin'
Option 2: Let Windows re-encrypt the file
If for some reason your OpenSSL installation does not contain the legacy provider:
Open PowerShell and run this command, replacing -FilePath with the path to your non-working pfx file, and the password -String argument with its respective password:
Import-PfxCertificate -FilePath "pfx file path" -CertStoreLocation Cert:\LocalMachine\My -Password (ConvertTo-SecureString -String 'MyPassword' -AsPlainText -Force) -Exportable
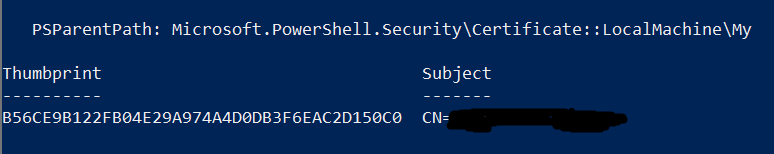
A successful output will look like:
![export pfx result]()
Use this thumbprint to export the cert to a new pfx file, replacing the -Cert, -FilePath, and password -String arguments:
Export-PfxCertificate -Cert Microsoft.PowerShell.Security\Certificate::LocalMachine\My\B56CE9B122FB04E29A974A4D0DB3F6EAC2D150C0 -FilePath 'newPfxName.pfx' -Password (ConvertTo-SecureString -String 'MyPassword' -AsPlainText -Force)
Azure should now be able to validate the new pfx file output.