I'm trying to follow the instructions in How can I allow a Group to assume a Role?, but run into the following error when I try to switch roles:
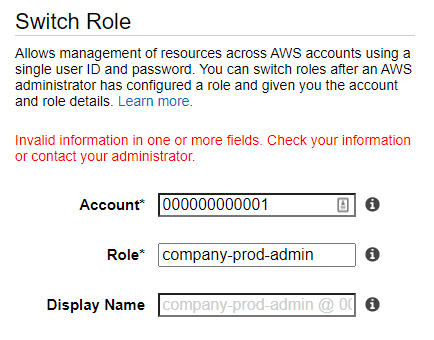
Invalid information in one or more fields. Check your information or contact your administrator.
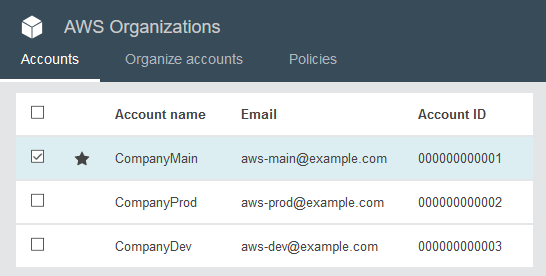
In this scenario I have three AWS Accounts with example ids
- CompanyMain -
000000000001 - CompanyProd -
000000000002 - CompanyDev -
000000000003
Where the main account has an organization that includes the the prod and dev accounts
What I'd like to do is set up a single set of IAM users on the main account and allow them to login and switch between either of the two subaccounts, instead of forcing everyone to have three separate logins.
Here's what I've done so far all on the CompanyMain account:
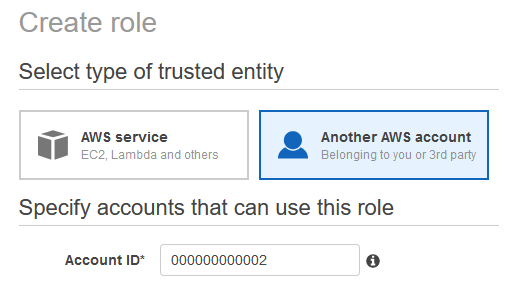
Create Role for accessing Prod Account
Set trusted Entity to "Another AWS Account"
Set Permission Policy to
AdministratorAccessSo when I go to Role > "Trust Relationship" > Show Policy Document - it looks like this:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::000000000002:root" }, "Action": "sts:AssumeRole", "Condition": {} } ] }With the name "company-prod-admin" so the ARN is like this:
arn:aws:iam::000000000001:role/company-prod-adminThis also comes with the link to switch roles as follows:
https://signin.aws.amazon.com/switchrole?roleName=company-prod-admin&account=000000000001
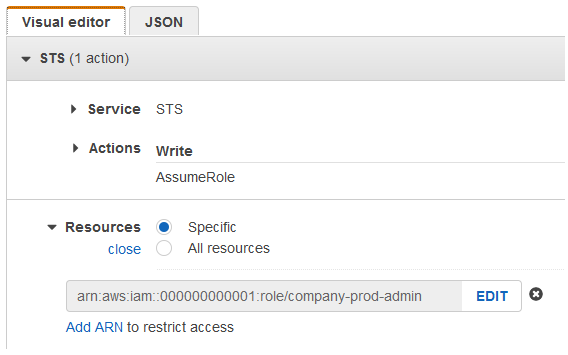
Create a Policy to Assume this Role
Service: STS Actions: AssumeRole Role ARN:
arn:aws:iam::000000000001:role/company-prod-adminSo the Policy Document looks like this:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": "arn:aws:iam::000000000002:root" } ] }Create Admin Group
Create a group on the main account called
adminand attach the policy we just createdCreate IAM User
Create user on the main account and place in
admingroup
Sign in as IAM User
I can now sign in as an IAM user against the main account
From there, I'd like to switch roles by using the role link or going to https://signin.aws.amazon.com/switchrole and entering the account / role info
However, I get the error that the following info is invalid
Org Setup Question
How can I create roles that across organizations? I'm a little confused as to where the role / permission needs to originate between the three accounts, but ideally I'd like to have a way for someone to login to one set of permissions for the whole organization.