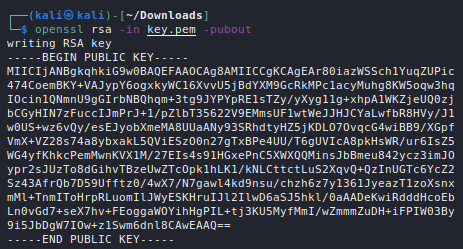
From whatever little I understand by reading various material, public-private key pair are the basis of asymmetric encryption and also something about choosing 2 prime numbers (which is roughly your private key) and multiplying them (which is roughly your public key). It appears to me that it is possible to generate a public key if you know the private key. Is it correct or I am mistaking something?
What made me more confusing was that it is not possible to serialize the RSA key to XML with only private key (using .NET class RSACryptoServiceProvider). Not sure whether this limitation is intentional or not!