So I had some luck with the following:
- Create a Managed Identity Scoped to
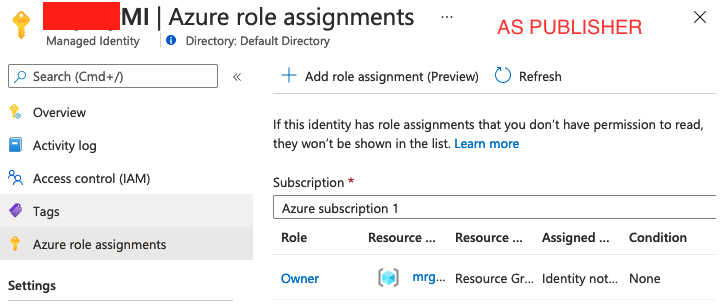
resourceGroup().id as Owner - this Identity seems to only be scoped to the Customer's Tenant (I was unable to perform anything with the Identity that required any kind of subscription/resource access... interestingly enough when logged in as a Publisher I can see this identity was granted Owner however logged in as a customer revealed nothing?
![Logged in as Publisher]()
![Logged in a Customer]()
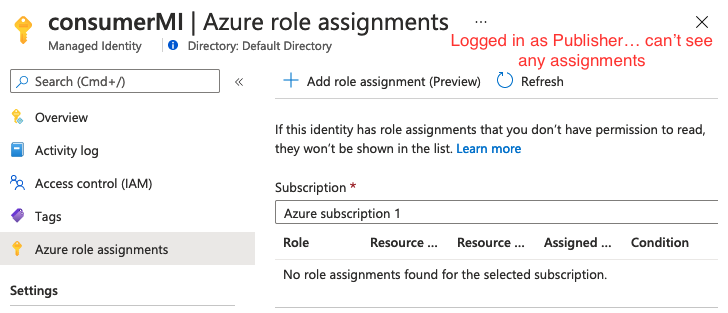
- Create a second Managed Identity - and put the (1) Managed Identity as the
delegatedManagedIdentityResourceId this seemed to generate a Managed Identity that is now scoped to the Customer so this second identity seems to be able to have roles assigned to it.
![The consumer Managed Identity from the Publisher's perspective]()
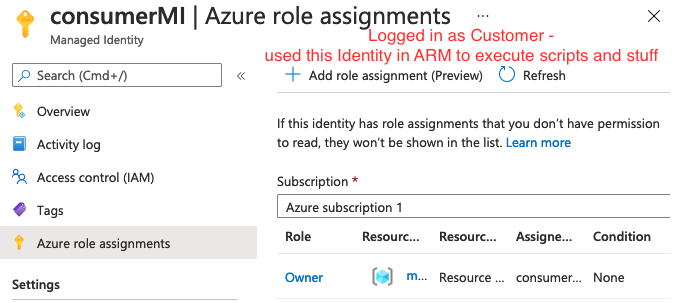
![Consumer Managed Identity view as a customer]()
I'm still not fully sure why I needed to do this... but now when I assign my consumer Managed Identity to a VM in my managed solution, this vm is able to access all the resources in the managed resource group. Whereas assigning the VM the first managed identity caused me problems.
ARM
{
"type": "Microsoft.ManagedIdentity/userAssignedIdentities",
"apiVersion": "2018-11-30",
"name": "publisherMI",
"location": "[parameters('location')]"
},
{
"type": "Microsoft.Authorization/roleAssignments",
"apiVersion": "2021-04-01-preview",
"name": "[guid('bootstrapRoleAssignmentId')]",
"dependsOn": [
"[resourceId('Microsoft.ManagedIdentity/userAssignedIdentities', 'publisherMI')]"
],
"properties": {
"roleDefinitionId": "[resourceId('Microsoft.Authorization/roleDefinitions/', '8e3af657-a8ff-443c-a75c-2fe8c4bcb635')]",
"principalId": "[reference(resourceId('Microsoft.ManagedIdentity/userAssignedIdentities', 'publisherMI'), '2018-11-30').principalId]",
"scope": "[resourceGroup().id]",
"principalType": "ServicePrincipal"
}
},
{
"type": "Microsoft.ManagedIdentity/userAssignedIdentities",
"apiVersion": "2018-11-30",
"name": "consumerMI",
"location": "[parameters('location')]"
},
{
"type": "Microsoft.Authorization/roleAssignments",
"apiVersion": "2021-04-01-preview",
"name": "[guid('consumerMiRoleAssignmentId')]",
"dependsOn": [
"[resourceId('Microsoft.ManagedIdentity/userAssignedIdentities', 'consumerMI')]",
"[resourceId('Microsoft.ManagedIdentity/userAssignedIdentities', 'publisherMI')]"
],
"properties": {
"roleDefinitionId": "[resourceId('Microsoft.Authorization/roleDefinitions/', '8e3af657-a8ff-443c-a75c-2fe8c4bcb635')]",
"principalId": "[reference(resourceId('Microsoft.ManagedIdentity/userAssignedIdentities', 'consumerMI'), '2018-11-30').principalId]",
"scope": "[resourceGroup().id]",
"principalType": "ServicePrincipal",
"delegatedManagedIdentityResourceId" : "[resourceId('Microsoft.ManagedIdentity/userAssignedIdentities', 'publisherMI')]"
}
},