I have been following the document: https://learn.microsoft.com/en-us/azure/databricks/dev-tools/api/latest/aad/service-prin-aad-token
to create a service principal and use it to access Databricks. I already have a databricks workspace configured and have used it to create a cluster. Then I've followed the process mentioned in the document, created a service principal and obtained the two tokens: AD Access token and management access token. However, I am unable to use the API.
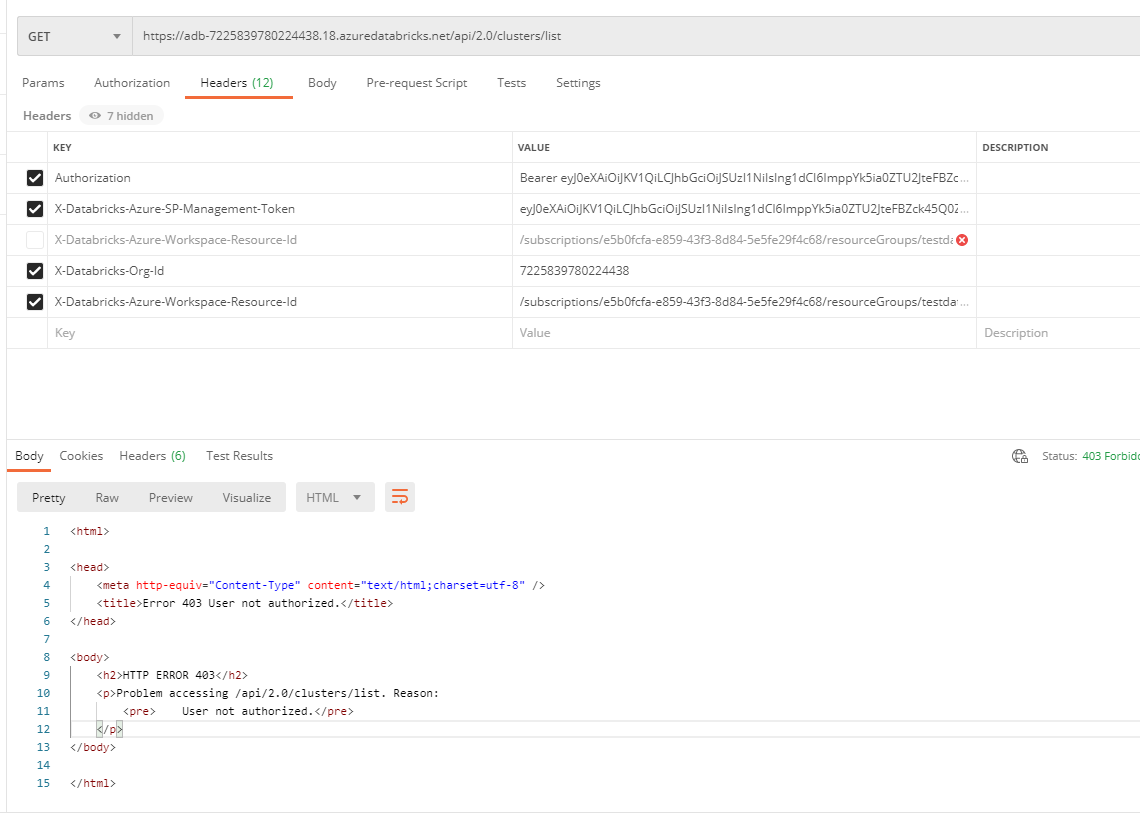
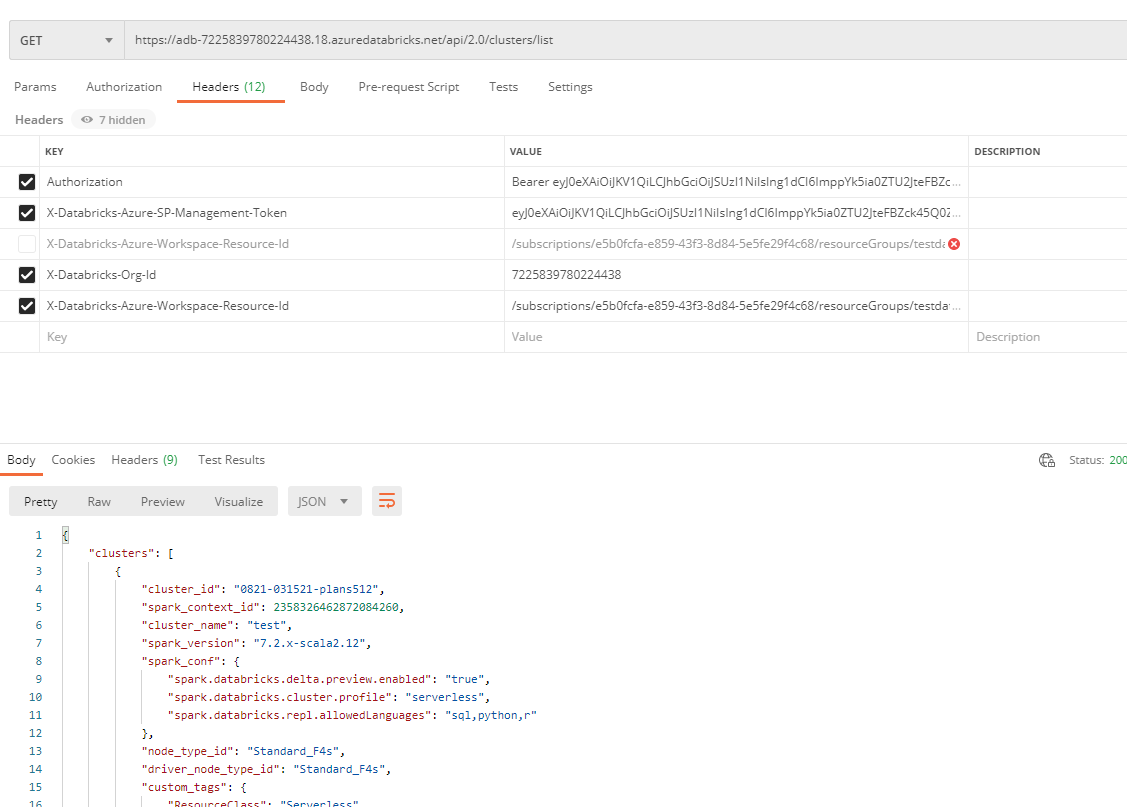
The final call cURL command after configuration:
curl -X GET \
-H 'Authorization: Bearer <access-token>' \
-H 'X-Databricks-Azure-SP-Management-Token: <management-access-token>' \
-H 'X-Databricks-Azure-Workspace-Resource-Id: /subscriptions/<subscription-id>/resourceGroups/<resource-group-name>/providers/Microsoft.Databricks/workspaces/<workspace-name>' \
https://<databricks-instance>/api/2.0/clusters/list
With the tokens and the other info substitutued provides the following result:
<html>
<head>
<meta http-equiv="Content-Type" content="text/html;charset=utf-8"/>
<title>Error 403 User not authorized.</title>
</head>
<body><h2>HTTP ERROR 403</h2>
<p>Problem accessing /api/2.0/clusters/list. Reason:
<pre> User not authorized.</pre></p>
</body>
</html>
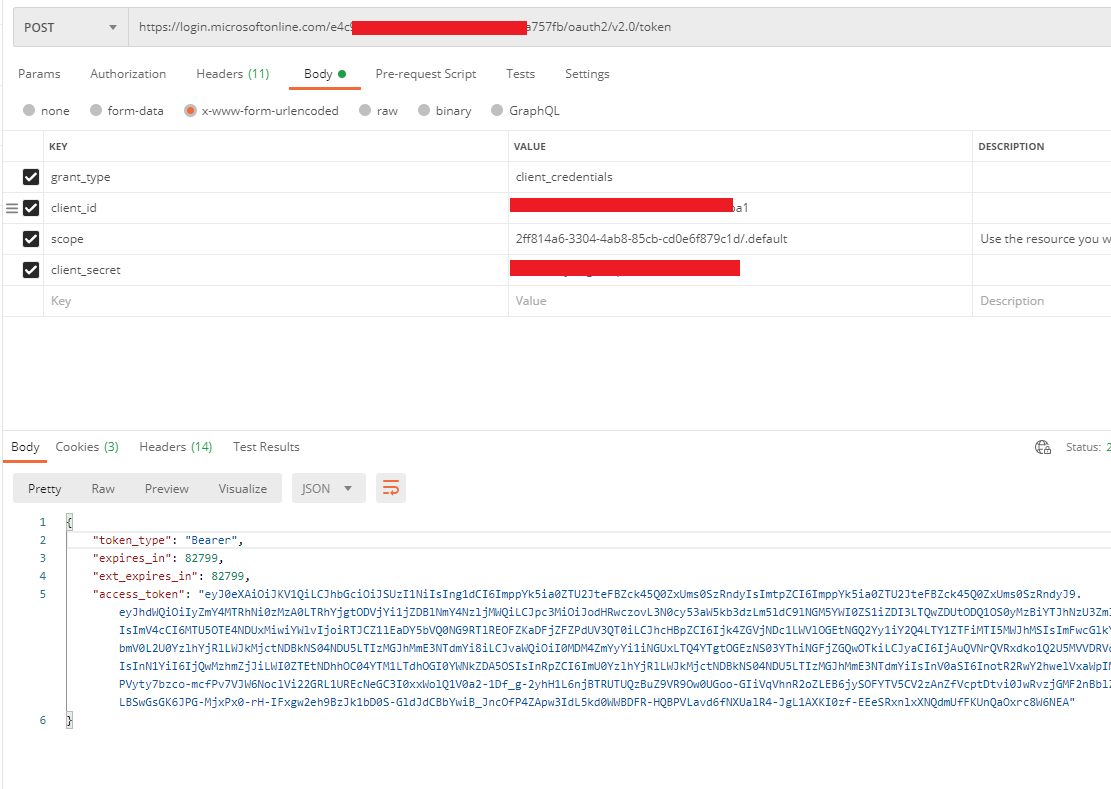
I have tried a couple of things to resolve this, namely changing the original access token request to use the interactive flow using the authorization_code grant type and so on, but that just gives me an Invalid access token error.
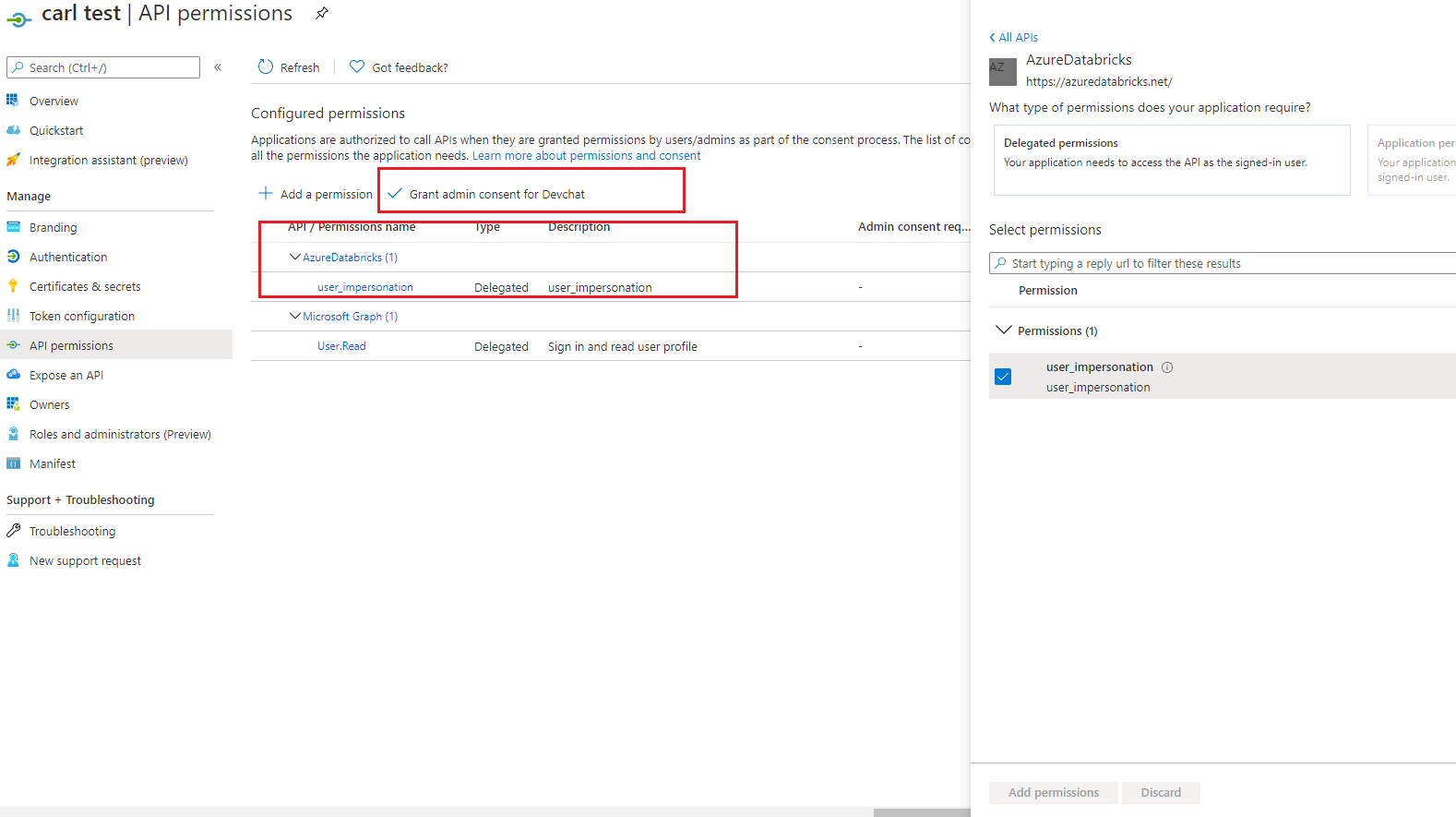
Is there something wrong with the above configuration? Am I missing some permissions?
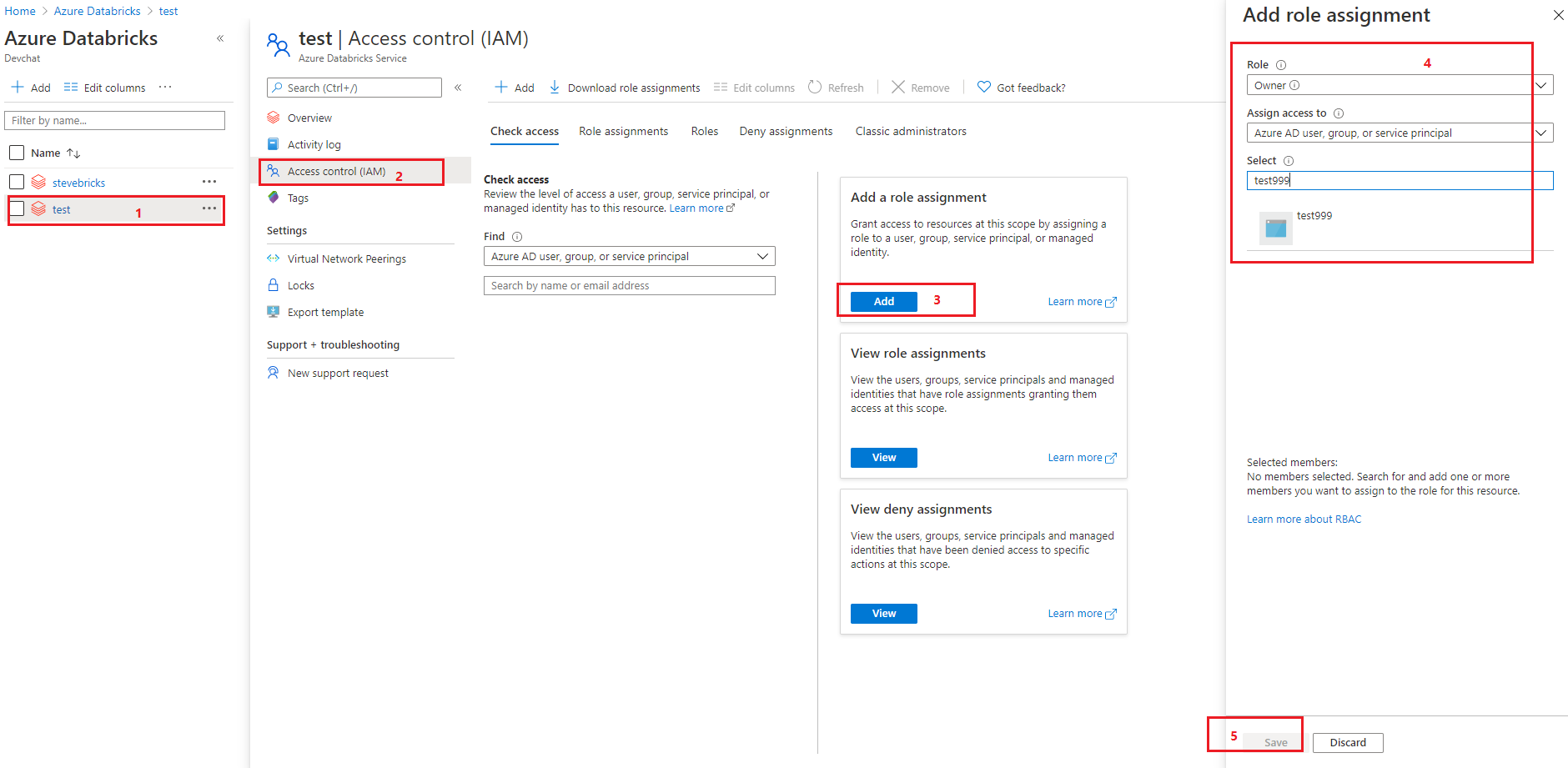
Update: Came to the Access control (IAM) page and the app does not seem to be included there.