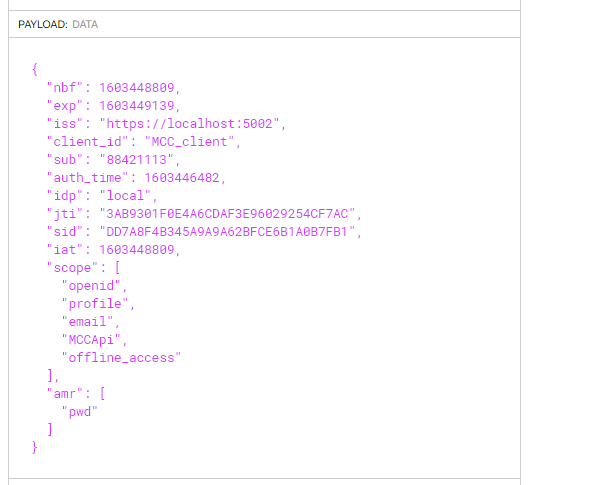
I have 3 projects 1- Angular SPA 2- Web API Project core 3.1, 3- IdentityServer with Core 3.1 But I am getting following error
> www-authenticate: Bearer error="invalid_token", error_description="The audience 'empty' is invalid"
This is my API startup
public void ConfigureServices(IServiceCollection services)
{
services.Configure<SchemaRegistryConfig>(Configuration.GetSection("SchemaRegistryConfig"));
//identity server
services.AddAuthentication(options =>
{
options.DefaultAuthenticateScheme = JwtBearerDefaults.AuthenticationScheme;
options.DefaultChallengeScheme = JwtBearerDefaults.AuthenticationScheme;
})
.AddJwtBearer("Bearer", options =>
{
options.Authority = "https://localhost:5002/";
options.RequireHttpsMetadata = false;
options.Audience = "Api";
});
IdentityModelEventSource.ShowPII = true;
services.AddCors(c =>
{
c.AddPolicy("AllowOrigin", options => options.AllowAnyOrigin().AllowAnyMethod().AllowAnyHeader());
});
services.AddMvc(config =>
{
config.Filters.Add(typeof(UnhandledExceptionFilter));
config.EnableEndpointRouting = false;
}).SetCompatibilityVersion(CompatibilityVersion.Latest);
services.AddServices(Configuration);
services.AddHealthChecksUI();
}
[Obsolete]
public void Configure(IApplicationBuilder app, IHostingEnvironment env)
{
if (env.IsDevelopment())
{
app.UseDeveloperExceptionPage();
}
else
{
app.UseHsts();
}
app.UseCors("AllowOrigin");
app.UseRouting();
app.UseAuthentication();
app.UseAuthorization();
app.UseHttpsRedirection();
app.UseMvc();
}
Identity server config.cs
public static class Config
{
public static IEnumerable<IdentityResource> IdentityResources =>
new IdentityResource[]
{
new IdentityResources.OpenId(),
new IdentityResources.Email(),
new IdentityResources.Profile(),
new IdentityResources.Address(),
new IdentityResource
{
Name = "Api",
//UserClaims =
//{
// "rc.garndma"
//}
}
};
public static IEnumerable<Client> Clients =>
new Client[]
{
new Client
{
ClientName = "Code Flow with refresh tokens",
ClientId = "_client",
AccessTokenLifetime = 330,// 330 seconds, default 60 minutes
IdentityTokenLifetime = 45,
AllowAccessTokensViaBrowser = true,
RedirectUris = new List<string>
{
"http://localhost:4200/*******"
},
PostLogoutRedirectUris = new List<string>
{
"http://localhost:4200/*******"
},
AllowedCorsOrigins = new List<string>
{
"http://localhost:4200"
},
RequireClientSecret = false,
AllowedGrantTypes = GrantTypes.Code,
RequirePkce = true,
AllowedScopes = { "openid", "profile", "email", "Api" },
AllowOfflineAccess = true,
RefreshTokenUsage = TokenUsage.OneTimeOnly
},
};
public static IEnumerable<ApiResource> GetApiResources()
{
return new List<ApiResource>
{
new ApiResource("Api", "Invoice API")
{
Scopes = { "invoice.read", "invoice.pay", "manage" }
},
};
}
public static List<ApiScope> ApiScopes()
{
return new List<ApiScope> {
new ApiScope(name: "read", displayName: "Reads your invoices."),
new ApiScope(name: "pay", displayName: "Pays your invoices."),
};
}
}
identity server startup.cs
public void ConfigureServices(IServiceCollection services)
{
services.AddControllersWithViews();
var builder = services.AddIdentityServer()
.AddInMemoryIdentityResources(Config.IdentityResources)
.AddInMemoryApiResources(Config.GetApiResources())
.AddInMemoryApiScopes(Config.ApiScopes())
.AddInMemoryClients(Config.Clients)
.AddTestUsers(TestUsers.Users);
services.AddAuthentication();
services.AddCors(options => options.AddPolicy("AllowAll", p =>
p.AllowAnyOrigin()
.AllowAnyMethod()
.AllowAnyHeader()));
// not recommended for production - you need to store your key material somewhere secure
builder.AddDeveloperSigningCredential();
}
public void Configure(IApplicationBuilder app)
{
if (Environment.IsDevelopment())
{
app.UseDeveloperExceptionPage();
}
app.UseStaticFiles();
app.UseRouting();
app.UseCors("AllowAll");
app.UseIdentityServer();
app.UseEndpoints(endpoints =>
{
endpoints.MapDefaultControllerRoute();
});
}
}
Angular SPA oidc config
export function configureAuth(oidcConfigService: OidcConfigService) {
return () =>
oidcConfigService.withConfig({
stsServer: 'https://localhost:5002',
redirectUrl: "http://localhost:4200/home",
postLogoutRedirectUri: window.location.origin,
clientId: '_client',
scope: 'openid profile email offline_access Api',
responseType: 'code',
silentRenew: true,
useRefreshToken: true
});
I have 3 controllers and I added [Authorize] on each controller. Can anyone help me with this? I get the token generated successfully and when I am using the token to call the webapi it throwing 401 with message. But no audience is present in it.