Depends on the type of token as to how it's consumed by the resource server.
Self encoded access tokens tokens (e.g. JWT bearer tokens) will contain all the user and scope information in the token. Or some Auth systems use token introspection as detailed in Jan's answer.
This is a good introduction to the resource server and the types of token.
And a very common self encoded token is the JWT Token.
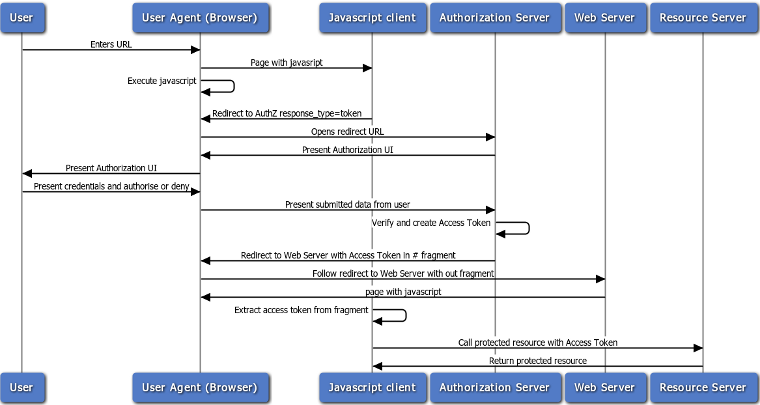
Taking the example of a self-encoded access token:
The Access Token will contain the user identifier and scopes / permissions for the token issued in the example above - which is the "implicit" grant type.
The Resource server should not need to contact the auth server. This can be one of the key benefits of Oauth 2.0 for APIs. It must trust it though. It should confirm the token has been signed by the auth server, and it may also need to be able to decrypt the token, if encrypted by the auth server.
Obviously the resource server needs to be able to access the data for the user in the token. It may be that the auth server and resource server point to the same underlying database.