From what I can tell TLS works using both symmetric and assymmetric encryption. The assymmetric schemes are used to exchange keys but when and what symmetric schemes are used?
The asymmetric schemes are used to exchange keys
and digital-signatures.
The symmetric schemes are used to data transfer with the agreed symnetric key during the key-exchange.
This is called Hybrid cryptosystem.
Yes you are right. Asymmetric algorithms are usually slower than the symmetric algorithms. However, symmetric algorithms require a shared secret key to encrypt and decrypt messages. Therefore, TLS allows the client and the server exchange a shared secret key using the asymmetric mechanism. Without an asymmetric algorithm, there is no way the shared secret can be exchanged between the two parties in a secured way. Once both the parties have the shared secret key, all subsequent communication between the client and the server are encrypted using the symmetric algorithm which is much faster than the asymmetric algorithm.
At a very high level, the steps in establishing a TLS connection looks like this:
- Client -> Requests for secured session
- Server -> Sends certificate & chain certificates
- Client -> Verifies certificate
- Client -> Generate random key for symmetric encryption
- Client -> Encrypts the generated key with the server public key and sends the encrypted value to the server
- Server -> Decrypt the client sent key with its own private key
Here onwards all subsequent communications between the server and the client will be encrypted using a symmetric algorithm.
Which specific algorithm will be used is determined by the cipher suites supported by the server and the client. During the connection setup, the cipher suite to be used is determined by the client preference.
A typical cipher suite name looks like this:
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
Here
ECDHE - Key exchange algorithm
ECDSA - Digital Signature algorithm used for signing the key
AES_128_GCM - Block cipher and mode with 128 bit key
ECDHE stands for Elliptic Curve Diffie Hellman Ephemeral. The Elliptic variant (the first E) is used for performance, whereas the Ephemeral variant (the last E) is for forward secrecy. Forward secrecy means that if an attacker keeps recording all the communications over TLS and at a later point of time somehow gets hold of the private key, he/she cannot decrypt the past recorded communications.
ECDSA is used for authenticating (verifying the integrity of) the shared secret. ECDSA is weaker and slower than the other authentication algorithms like HMAC. Yet it is used for shared key authentication because it does not need the verifier know the secret key used to create the authentication tag. The server can very well use its private key to verify the integrity of the message.
AES_128_GCM - Once a common secret key is shared between both the parties (usually a browser and a web server), a symmetric block cipher algorithm is used to encrypt the message exchanges between the parties. In this particular case, the block cipher AES with 128 bit key and GCM authentication mode is used.
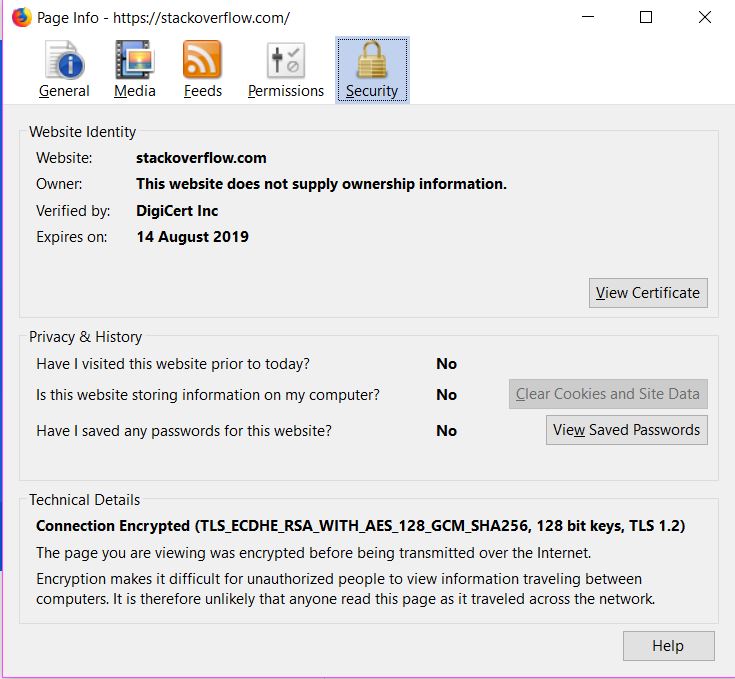
If you open a HTTPS website in a browser, you can see the cipher suite used using the browser utilities. For e,g, in Firefox you can see the details under the Security tab in the Page Info, as shown below:
© 2022 - 2024 — McMap. All rights reserved.